Experts at Rapid7 have disclosed a critical vulnerability affecting 689 Brother printer models and 53 models from other manufacturers, including Fujifilm, Toshiba, and Konica Minolta. The flaw lies in a predictable algorithm used to generate administrator passwords—an issue that cannot be fully resolved on already released devices through firmware updates.
Designated as CVE-2024-51978, the vulnerability has been assigned a severity score of 9.8 on the CVSS scale. It enables threat actors to deduce the default administrative password and gain full control over the device. According to researchers, the weakness stems from an insecure algorithm implemented during the manufacturing process.
The technical breakdown reveals that the password is generated by extracting the first 16 characters of the device’s serial number, appending eight bytes from a static value table, and hashing the result using SHA-256. The hash is then Base64-encoded, and the first eight characters of the encoded string—some of which are substituted with special characters—form the final password. This process, specialists warn, is easily reversible, rendering the protection mechanism dangerously fragile.
Additionally, researchers uncovered seven more vulnerabilities affecting Brother and other printers, including information leaks, stack overflows, forced TCP connections, and potential device crashes. Some of these issues can be exploited without prior authentication.
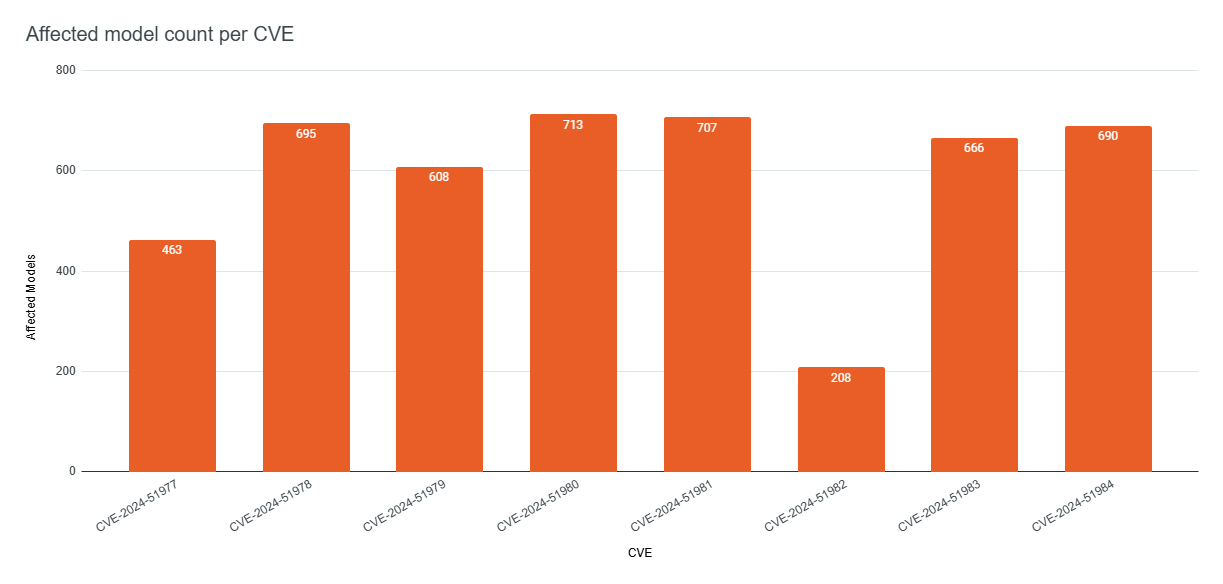
The full list of vulnerabilities includes:
- CVE-2024-51977 – Information disclosure (CVSS 5.3)
- CVE-2024-51978 – Critical flaw with predictable admin passwords (CVSS 9.8)
- CVE-2024-51979 – Stack overflow via authenticated access (CVSS 7.2)
- CVE-2024-51980 & CVE-2024-51981 – Forced TCP connection or arbitrary HTTP request (CVSS 5.3 each)
- CVE-2024-51982 & CVE-2024-51983 – Potential device crash (CVSS 7.5 each)
- CVE-2024-51984 – External service password disclosure (CVSS 6.8)
When combined, these vulnerabilities could allow attackers not only to gain administrative access, but also to alter device settings, exfiltrate data, execute remote code, disable equipment, or pivot further into the target network.
Rapid7’s findings indicate that the critical flaw CVE-2024-51978 affects not only Brother devices but also dozens of models from other manufacturers: 46 from Fujifilm, six from Konica Minolta, five from Ricoh, and two from Toshiba. However, the presence of all eight vulnerabilities varies by model.
Brother has acknowledged the issue, stating that CVE-2024-51978 cannot be fully addressed through software updates alone. A permanent fix would require alterations in the hardware manufacturing process. Consequently, already distributed printers remain vulnerable unless users manually change the default password.
The disclosure process began in May 2024. With the assistance of Japan’s coordination center JPCERT/CC, Rapid7 informed the vendors and supported the release of patches. Nevertheless, the fundamental flaw of predictable passwords remains unfixable in existing units.
Owners of affected printer models are strongly advised to change the default administrative password immediately and install all available firmware updates. Furthermore, access to administrative interfaces should be restricted from external and unsecured networks.
Official websites for Brother, Konica Minolta, Fujifilm, Ricoh, and Toshiba now provide guidance and updates aimed at mitigating exploitation risks.






