Hackers have ramped up their attacks on vulnerable Linux servers with exposed SSH access, deploying the SVF Botnet—a simple yet effective malicious framework designed for conducting DDoS attacks and cryptocurrency mining. This revelation comes from the AhnLab Security Intelligence Center (ASEC), which monitors such threats using specially configured honeypot servers.
One of the most recent incidents involved an attack on one of these honeypots. Threat actors exploited weak login credentials through brute-force techniques and, upon gaining SSH access, swiftly deployed the botnet malware. At the core of this malicious infrastructure lies a Python script associated with an informal group calling itself the “SVF Team.”
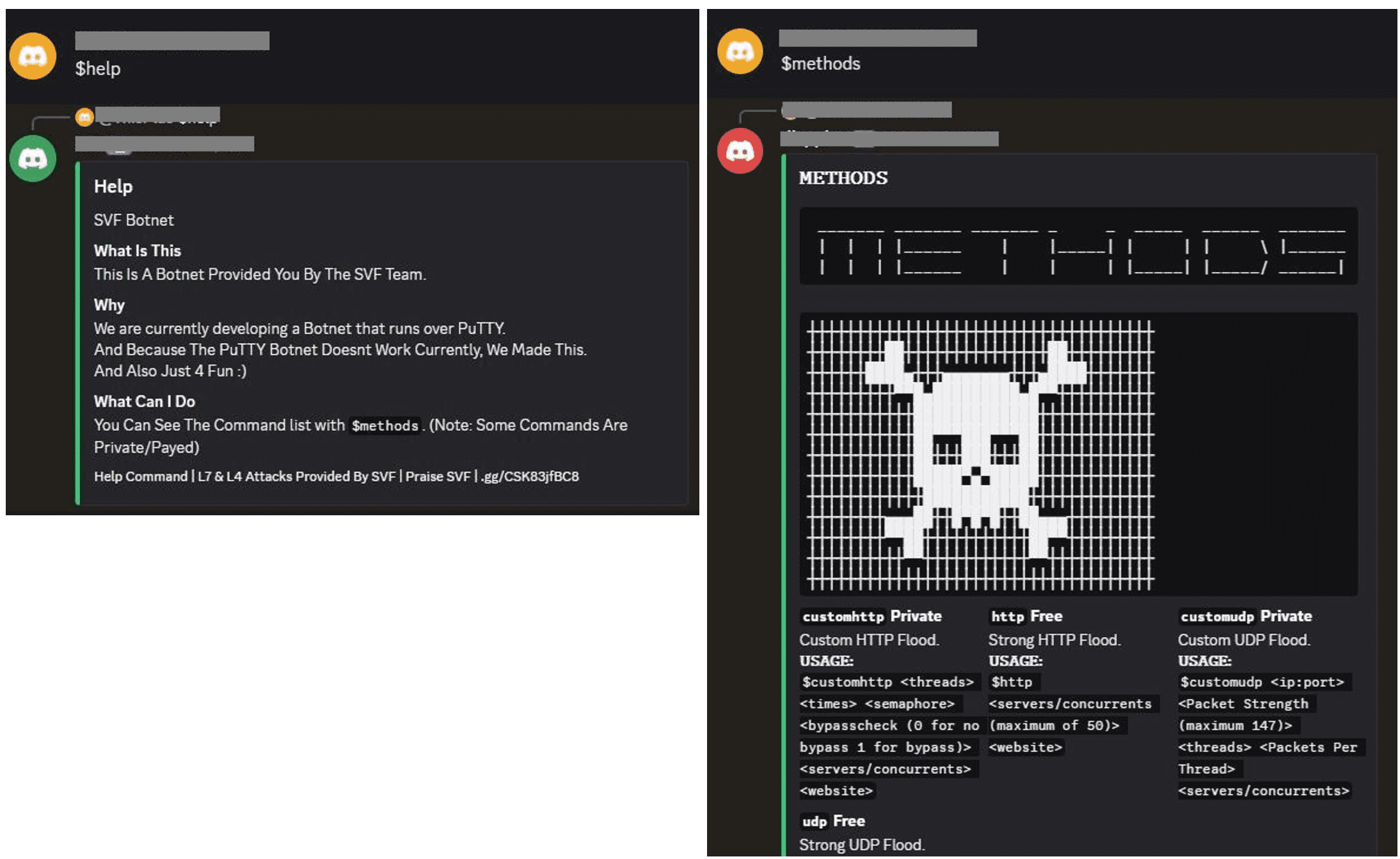
A particularly notable aspect of the operation is its use of Discord—a messaging platform popular among gamers and youth—as its command-and-control (C2) channel. Through this medium, the bot receives instructions and transmits data about the infected system.
The installation process of the SVF Botnet is centered around setting up a virtual environment, into which essential dependencies are installed, including the libraries discord.py, requests, aiohttp, and lxml. The primary script, main.py, is then fetched from the termbin service and executed with specific parameters, such as -s 5, enabling simultaneous control of multiple compromised machines within a single botnet instance.
Once activated, the bot authenticates using a Discord token and connects to the designated control channel, from which it receives operational commands. It also reports its status—including group affiliation—via webhooks, allowing the botnet operators to maintain a segmented, modular command architecture.
SVF’s capabilities are focused on two primary attack vectors: HTTP floods (Layer 7) and UDP floods (Layer 4). The botnet allows extensive customization, including thread count, packet intensity, and attack concurrency. Perhaps most impressive is its built-in proxy system: the bot autonomously scrapes proxy lists from GitHub and other public sources, validates them by attempting logins on Google, and rotates among working proxies during attacks—complicating attribution and evading defensive measures.
Among the arsenal of commands ($load, $customhttp, $customudp) are features for dynamically loading new proxies, initiating tailored attack profiles, and halting active operations. Additional functionalities include bot restarts, fault recovery mechanisms, and the ability to fetch updated versions from a designated IP address—indicating a continuously evolving and increasingly sophisticated malware ecosystem.
This incident underscores the persistent vulnerability of Linux servers with poorly secured SSH configurations. Once compromised, a server becomes an unwilling node in a broader botnet, its resources diverted toward malicious campaigns. To prevent such breaches, system administrators are urged to enforce robust authentication practices—such as employing long, unique passwords, rotating them regularly, applying the latest security patches, and restricting SSH access through firewalls.
Moreover, the timely updating of antivirus and endpoint protection solutions remains crucial for the detection of emerging threats. As adversaries increasingly leverage open-source tools and repurpose legitimate services for obfuscation, the deployment of honeypot infrastructures and the continuous monitoring of suspicious activity remain essential strategies for intelligence gathering and fortifying cyber resilience.






