A security researcher uncovered critical vulnerabilities in the admin panel of Pudu Robotics, China’s largest supplier of commercial service robots. The flaw allowed attackers to redirect robots and issue arbitrary commands.
Pudu manufactures over 100,000 machines deployed across more than a thousand cities worldwide, ranging from the cat-shaped BellaBot used in restaurants to the FlashBot equipped with mechanical arms capable of operating elevators and other systems. According to Frost & Sullivan, the company holds a 23% share of the global service robot market.
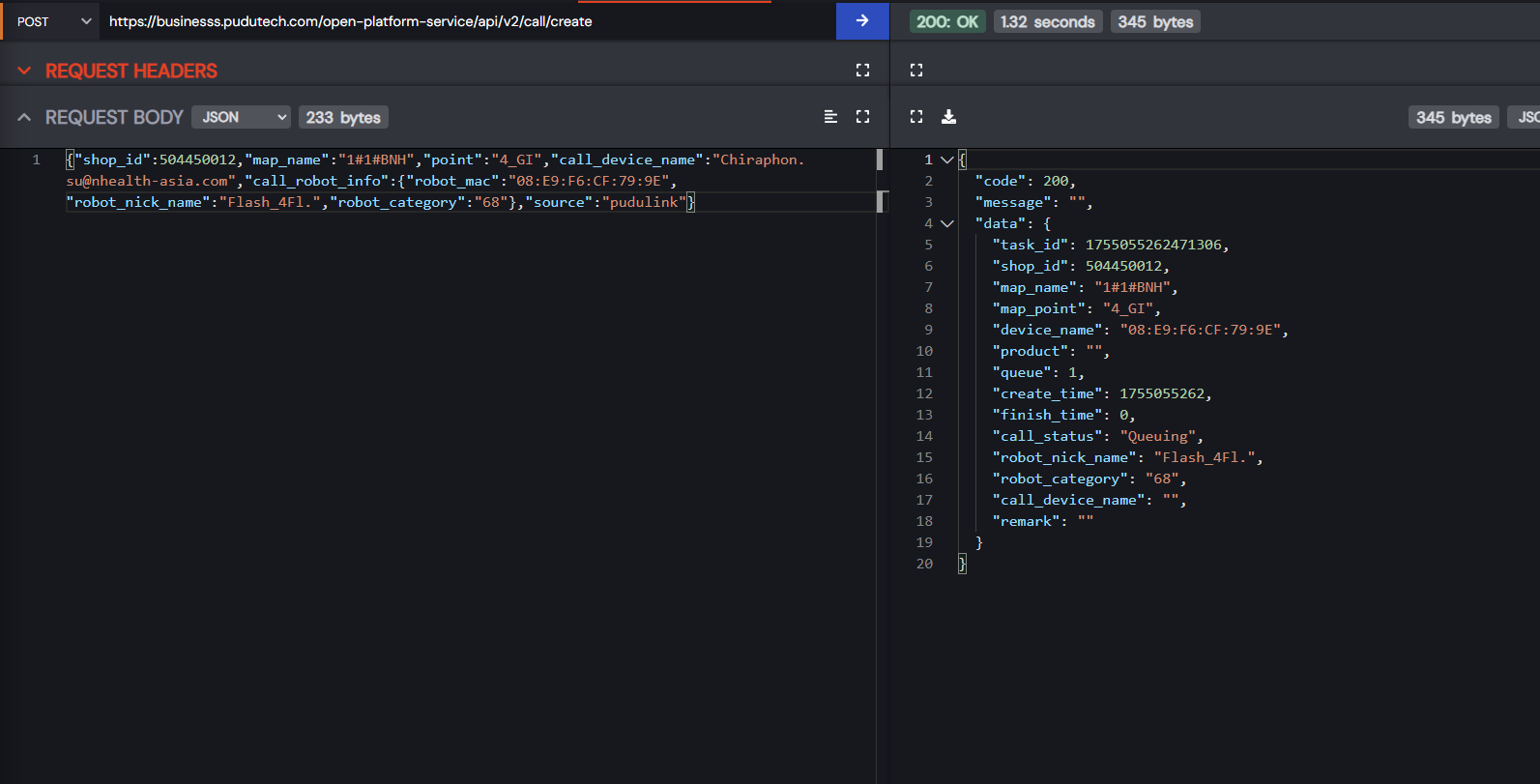
White-hat hacker Bobdahacker, who had previously disclosed a vulnerability in McDonald’s ordering system, examined Pudu’s control software. She discovered that administrators had failed to restrict access: once an authorization token was obtained, full control of the robots was possible.
Such a token could be stolen via an XSS attack or acquired by registering a test account as a potential client. After logging in, no additional checks were enforced, enabling attackers to alter orders, redirect robots, and even rename them, complicating recovery efforts.
With this level of access, adversaries could have diverted food deliveries, halted entire fleets of restaurant robots in a “food DDoS attack,” forced FlashBots to disrupt office infrastructure, or even stolen intellectual property.
On August 12, the researcher reported the flaw to Pudu, but her warning was ignored by the company’s support, service, and sales teams.
Days later, she emailed over 50 employees, yet still received no response.
The situation shifted only after Bobdahacker contacted Pudu’s clients. Major Japanese chains Skylark Holdings and Zensho treated the warning seriously, prompting the manufacturer to finally engage.
The reply arrived 48 hours later but appeared to be an auto-generated template—complete with the placeholder [Your Email Address] still visible. Frustrated, the researcher published her findings on her blog.
Ultimately, Pudu patched the vulnerability and reinforced its defenses, though the company has issued no public statement on the matter.