A new tool for disabling EDR systems has emerged in the cybercriminal underground, which Sophos researchers regard as an evolution of the EDRKillShifter utility. Its use has already been documented in attacks by eight distinct threat groups, including RansomHub, BlackSuit, Medusa, Qilin, Dragonforce, Crytox, Lynx, and INC. Such programs enable ransomware operators to incapacitate security solutions on compromised devices, allowing them to deploy payloads unhindered, escalate privileges, move laterally across networks, and ultimately encrypt data without the risk of detection.
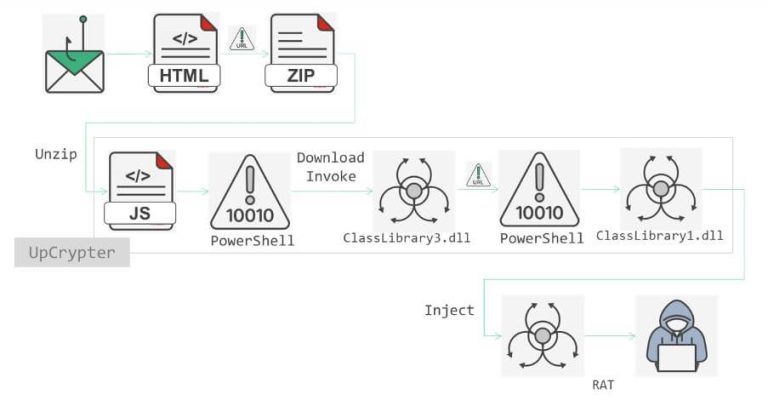
The new EDR Killer is a heavily obfuscated binary that self-decodes at runtime and injects itself into legitimate processes. In its next phase, the utility searches for a digitally signed driver with a stolen or expired certificate and a random five-character name hardcoded into the executable. If such a driver is located, it is loaded into the kernel, enabling the Bring Your Own Vulnerable Driver (BYOVD) technique to obtain the system-level privileges necessary to disable security products.
Masquerading as legitimate components — for instance, a CrowdStrike Falcon Sensor driver — the malicious driver terminates antivirus and EDR processes and halts associated services. Solutions from Sophos, Microsoft Defender, Kaspersky, Symantec, Trend Micro, SentinelOne, Cylance, McAfee, F-Secure, HitmanPro, and Webroot are among the targets. Variants of the tool differ in driver names, targeted product lists, and build characteristics, but all employ the HeartCrypt packer. According to Sophos, this is not a one-off leaked binary but a collaboratively developed platform, used even by competing groups — each with its own tailored build.
The practice of sharing such tools within the ransomware ecosystem is well established. Beyond EDRKillShifter, Sophos has previously identified other utilities of this class, such as AuKill, used by Medusa Locker and LockBit. Last year, SentinelOne also reported that the FIN7 group had sold its AvNeutralizer tool to multiple gangs, including BlackBasta, AvosLocker, MedusaLocker, BlackCat, Trigona, and LockBit. A full list of indicators of compromise (IOCs) for the new EDR killer is available in a public GitHub repository.