Researchers at Varonis Threat Labs have uncovered a new phishing campaign in which attackers exploit a little-known Microsoft 365 feature known as Direct Send. Originally intended for sending emails from internal devices such as printers without requiring authentication, this feature has been repurposed by malicious actors to spoof internal addresses and distribute phishing emails—without needing to compromise any user accounts.
According to Varonis, the campaign began in May 2025 and has already impacted more than 70 organizations, primarily within the United States. The attacks were targeted, and the emails raised little suspicion, as they appeared to originate from within the organization. Common threads among the incidents included identical subject lines, matching sender IP addresses, and other technical fingerprints. Security experts have long noted similar patterns in Microsoft 365-related attack vectors.
The crux of the issue lies in Direct Send’s ability to relay emails through Microsoft’s internal mail gateway without the use of passwords or authentication tokens. All an attacker needs is the organization’s domain name and a single internal email address—details that can be easily guessed or harvested from public sources.
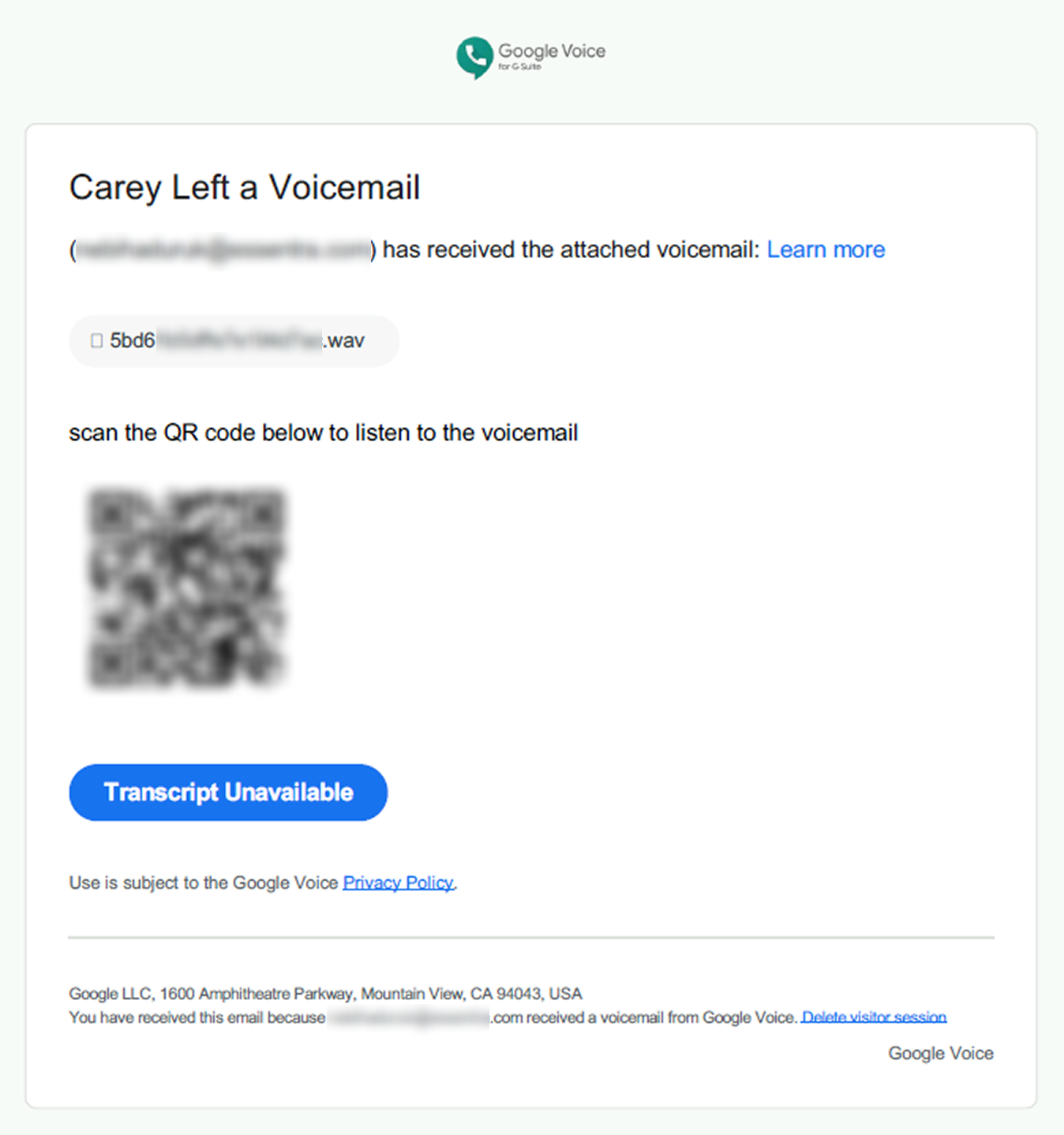
In the cases investigated by Varonis, the emails were sent via PowerShell and disguised as voicemail or fax notifications. Each message included a PDF attachment containing a QR code that redirected recipients to phishing sites designed to steal Microsoft 365 credentials. The use of QR codes in phishing campaigns is becoming an increasingly favored tactic among cybercriminals. Despite lacking digital signatures and failing SPF and DMARC validation, the emails nonetheless passed through Microsoft’s infrastructure and landed directly in employees’ inboxes.
In some instances, security systems were triggered when messages originated from unusual IP geolocations—such as Ukraine—but it was the outbound activity, not login attempts, that raised red flags. Email header analysis revealed that, although the messages came from external sources, they employed internal routing, allowing them to bypass filtering mechanisms effectively.
To guard against such attacks, experts recommend disabling the Direct Send feature, enforcing strict DMARC policies, monitoring unauthenticated messages, applying anti-spoofing rules, and educating employees about the dangers of malicious attachments—particularly those using QR codes. Proper configuration of SPF and DMARC is critical for preventing sender impersonation. Multi-factor authentication and restricting allowable IP addresses in SPF records are also essential.
Varonis emphasizes that even internal-looking emails can pose a significant threat if such loopholes remain unmonitored. Their suite of tools and real-time detection capabilities is designed to identify and neutralize these threats as they emerge.




