Country-based targeting
In a sweeping espionage campaign dubbed LapDogs, over a thousand small office and home office devices were compromised. Researchers from the STRIKE team at SecurityScorecard reported that the attack was linked to Chinese threat actors and aimed to construct a covert network supporting long-term cyber intelligence operations. The hijacked devices were assimilated into an infrastructure named Operational Relay Box (ORB), which facilitated persistent communication and masked the presence of command-and-control servers.
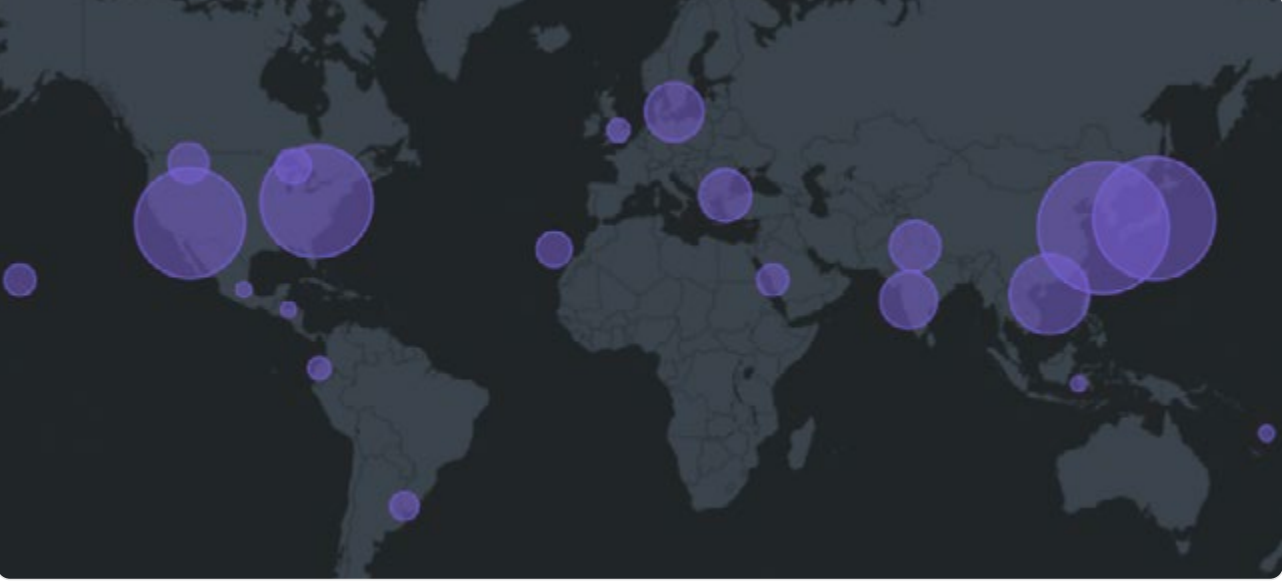
According to the report, primary targets of the campaign were located in the United States, Japan, South Korea, Hong Kong, Taiwan, and nations across Southeast Asia. The researchers attributed the operation to the Chinese-affiliated group UAT-5918, based on the language found within the malware, victim profiling, and overlaps with previous attacks on critical infrastructure.
The STRIKE team managed to obtain a sample of the Linux-based malware known as ShortLeash. The script required root privileges, identified the operating system (Ubuntu or CentOS), and embedded itself into system autostart processes. If the OS was unrecognized, a Chinese-language message would appear. Upon execution, the script replaced a core system service to remain hidden from users and antivirus tools. The malware was encrypted in two layers, revealing upon decryption a payload containing certificates, private keys, and a control-server URL—disguised as a standard Nginx web server.
LapDogs did not confine itself to specific brands. Devices from ASUS, D-Link, Microsoft, Panasonic, Synology, and others were among the victims. The decisive factor for infection was the operating system, not the device type. Systems with GoAhead web interfaces, WRT admin panels, and IIS servers were especially vulnerable.
Many devices enlisted in the LapDogs network were exposed due to outdated software versions, including mini_httpd and DropBear SSH. The attackers exploited long-known vulnerabilities, such as CVE-2015-1548 and CVE-2017-17663. Most compromised devices ran lightweight web servers, typical of embedded systems and routers.
An analysis of the digital certificates—created with near-simultaneous timestamps down to the second—revealed the automated nature of the attacks. Using AI, researchers identified 162 distinct clusters of infected devices, many with striking geographic and ISP-based commonalities. In several cases, over 95% of devices in a cluster shared the same provider and were located in the same city, indicating deliberate geographic targeting.
The campaign has likely been ongoing since at least September 2023 and appears to be expanding methodically. Though most infected clusters are relatively small—fewer than 60 devices—research indicates the operation is carefully orchestrated, selective, and designed for prolonged activity.
LapDogs bears similarities to a campaign named PolarEdge, previously uncovered by Sekoia. Both operations exploit routers and IoT devices, but LapDogs exhibits broader scope, incorporating virtual servers and even Windows machines. A variant of ShortLeash for Windows was identified, including versions compatible with legacy systems like Windows XP.
While attribution remains inconclusive, available indicators point toward Chinese involvement. The use of Chinese within scripts and the alignment of targeting with Chinese geopolitical interests suggest state-linked coordination. Analysts speculate that the ORB network may be shared among multiple groups, and its access could eventually be extended to additional threat actors.
According to SecurityScorecard experts, such infrastructures undermine conventional methods for detecting and mitigating cyber threats. They urge security teams to adapt to the evolving tactics employed by Chinese cyber-espionage actors and to prepare for a new paradigm in digital intelligence operations.