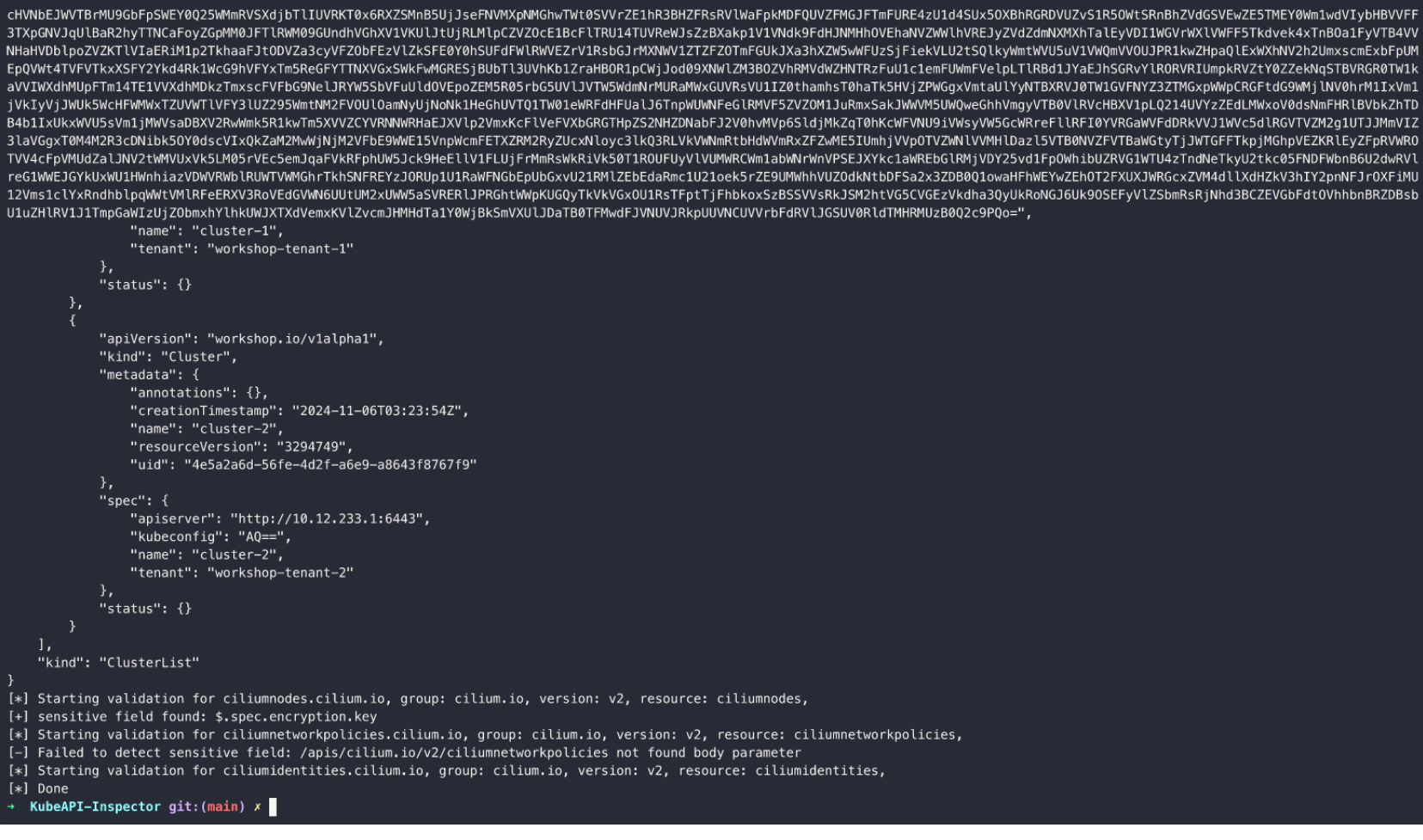
A tool specifically designed for Kubernetes environments aims to efficiently and automatically discover hidden vulnerable APIs within clusters. It reveals and demonstrates a common error through a workshop format, which could lead to API endpoint authentication failures and potentially compromise the entire cluster. The workshop can be deployed using Kubernetes resource YAML files.
Features
Implemented in Inspector
- 【✅】Automatically parse OpenAPI to identify sensitive fields
- 【✅】Automatically detect potential authentication bypass APIs
- 【✅】Automatically load credentials from the environment
To be Implemented in Inspector
- 【 】Automatically discover services and detect potential vulnerabilities in extension API servers
- 【 】exploitation of known control plane components?
Implemented in Workshop
- 【✅】Flawed implementation of the REST layer
To be Implemented in Workshop
- 【 】Typical vulnerabilities involving operator controllers
Installation
Requirements
- golang>1.22
- kubernetes and docker
- linux-amd64, linux-arm
build kubeapi-inspector
CWD: /repo/
- use go build
CGO_ENABLED=0 GOOS=linux GOARCH=amd64 GO111MODULE=on go build -o inspector cmd/inspector/main.go - or use docker to build
docker build . -t inspector:latest
build & deploy workshop steps
CWD: /repo/workshop/
- setup a kubernetes cluster, maybe you should use minikube, e.g.
minikube start --kubernetes-version='v1.23.17' - build workshop image with docker
docker build . -t workshop-apiserver:latest - deploy etcd for workshop-apiserver
cd workshop/examples/etcd && ./generate-certs.sh && deploy.sh - create workshop k8s resource
cat examples/{namespace,apiserviceservice,workshop-apiserver-sa,workshop-apiserver-clusterrolebinding,workshop-apiserver-deployment}.yaml | kubectl apply -f - - create demo cluster resource and tenant accounts
kubectl apply -f examples/tenant
Usage

in-cluster
- download binary in pod
- run binary
./inspector
out-of-cluster
./inspector -kubeconfig path/to/kubeconfig- test other namespace
./inspector -kubeconfig path/to/kubeconfig -namespace kube-system - skip sensitive field test
./inspector -kubeconfig path/to/kubeconfig -skipCheckSensitiveField=true