Since its emergence in the spring of 2024, the ransomware-as-a-service (RaaS) group Embargo has rapidly secured a prominent position in the cybercriminal landscape. According to TRM Labs, wallets linked to the operation may have received approximately $34.2 million USD, with most victims based in the United States and representing the healthcare, business services, and industrial manufacturing sectors. In certain cases, ransom demands reached as high as $1.3 million.
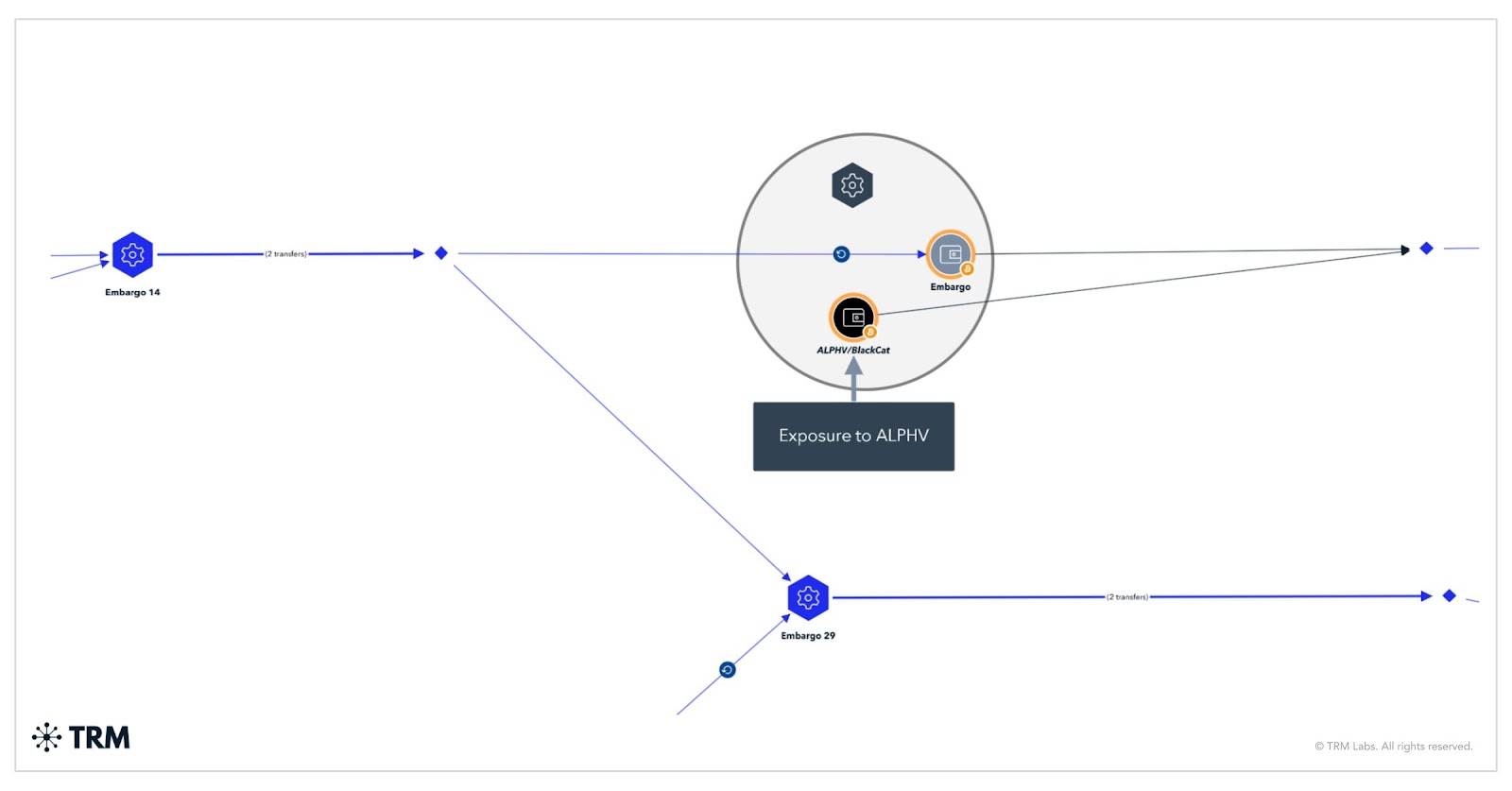
TRM assesses that Embargo may be a rebranded or successor entity to BlackCat (ALPHV), a theory supported by both technical and behavioral similarities. Both groups employ the Rust programming language, share a comparable design for data-leak sites, and exhibit overlaps in cryptocurrency infrastructure. A significant portion of the proceeds flows through intermediary wallets, high-risk exchanges, and even sanctioned platforms, including Cryptex.net. Roughly $18.8 million remains in unattributed addresses—likely reflecting a deliberate strategy of delaying transactions to hinder tracking efforts.
Embargo’s technical capabilities suggest the use of artificial intelligence and machine learning to scale attacks, craft more persuasive phishing emails, modify malicious code, and accelerate operations. As with other RaaS groups, cryptocurrency—predominantly Bitcoin, and occasionally Monero—plays a central role in ransom operations. Despite growing law enforcement efforts to trace transactions, criminals continually adapt their methods to evade detection.
Operating on a model in which it provides tools to affiliated hackers while retaining control over infrastructure and ransom negotiations, Embargo can scale attacks quickly across diverse regions. The group avoids excessive public pressure on victims and refrains from overly noisy tactics, reducing media and law enforcement attention. Nonetheless, its methods remain aggressive: employing double extortion through both encryption and data theft, publishing victims’ names and personal details on leak sites, and occasionally issuing politically charged statements—complicating attribution and raising questions about possible state affiliations.
The group’s primary focus is on organizations highly dependent on uninterrupted operations—particularly in healthcare, where disruptions can endanger patient lives. Geographically, the United States remains the priority target, perceived as offering greater potential for substantial payouts. Initial access is typically gained through unpatched vulnerabilities and social engineering—ranging from phishing emails to drive-by downloads. Once inside, attackers deploy tools to disable security measures, delete backups, and communicate through Embargo-controlled channels.
TRM’s findings indicate that Embargo prefers multi-stage laundering through wallet chains rather than heavy reliance on mixers. Deposits to global exchanges have exceeded $13 million, with a portion of transactions routed through Cryptex.net. Transaction delays, interim storage of funds, and the distribution of assets among affiliates suggest a deliberate and sophisticated financial strategy.
With AI now integrated into the arsenals of RaaS groups, operations like Embargo gain tools for automating reconnaissance, vulnerability scanning, malware generation, and even producing deepfakes of company executives to bolster social engineering campaigns. At the same time, AI also serves as a defensive countermeasure—enabling systems capable of detecting anomalous network behavior and early signs of data encryption.
Embargo exemplifies how modern ransomware blends technical sophistication, calculated financial maneuvering, and adaptation to political contexts. Effective countermeasures demand a combination of robust technological defenses, continuous software patching, staff training, international cooperation, and precise, timely threat intelligence.