A newly evolved strain of the Coyote banking trojan has adopted an unconventional method of user surveillance on Windows systems. Malicious actors have learned to exploit Microsoft’s UI Automation (UIA) framework—originally designed to aid users with disabilities—to monitor visits to banking websites and cryptocurrency exchanges. This technique enables the malware to harvest sensitive data, including login credentials, while bypassing modern security mechanisms.
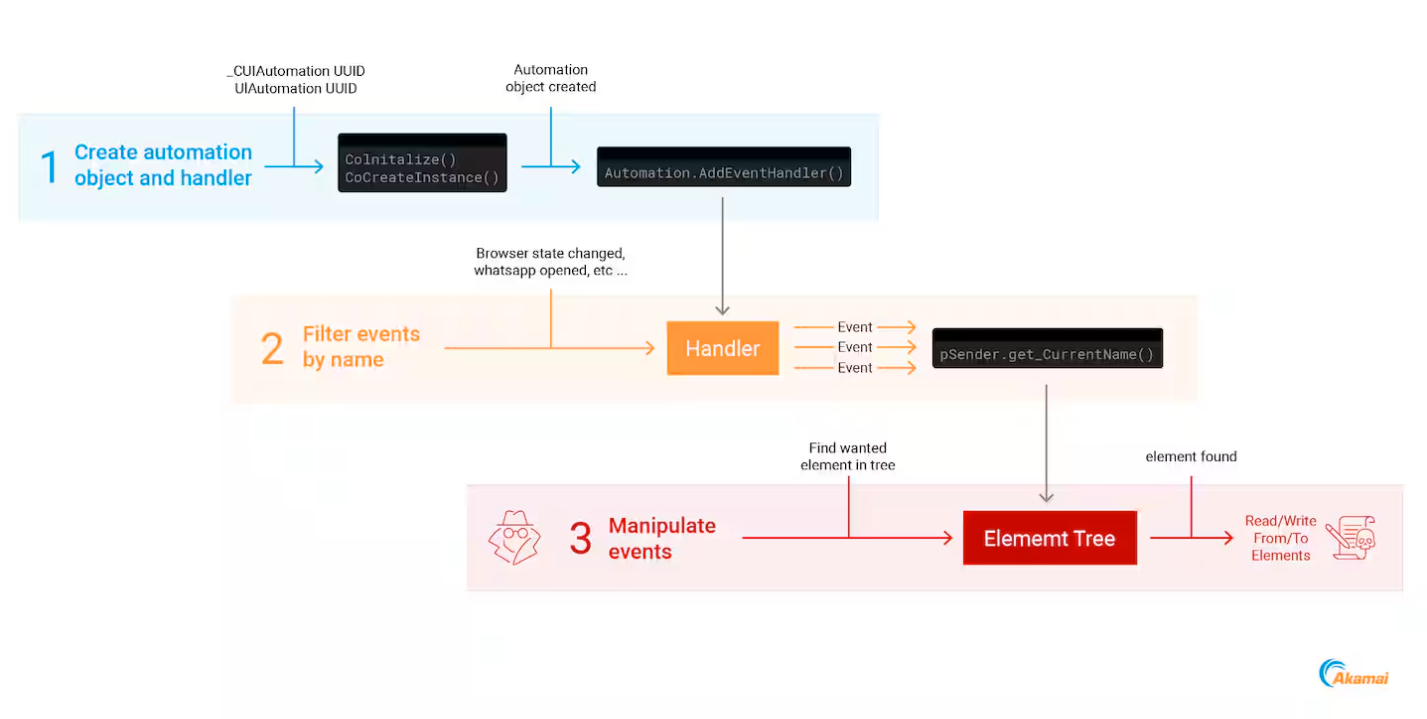
The UIA platform was developed to facilitate interaction between assistive technologies—such as screen readers—and user interface elements in Windows applications. UIA-compatible software constructs what is known as an automation tree, wherein each element (button, window, tab) can be detected, analyzed, and even manipulated externally via a specialized API. While this architecture has empowered the creation of accessible computing experiences, its versatility and power have also attracted the interest of cybercriminals.
Experts at Akamai first warned of the potential for such abuse in December 2024, hypothesizing that UIA could be leveraged to evade Endpoint Detection and Response (EDR) solutions, since the framework is deemed “safe” and does not typically trigger antivirus alerts. As of February 2025, this theoretical risk has materialized into active exploitation. It marks the first documented case in which a trojan has harnessed UIA capabilities to steal data directly from a victim’s system.
Originally discovered in February 2024, the Coyote trojan has since undergone significant evolution. It primarily targets users in Brazil and is capable of stealing credentials from 75 financial institutions and cryptocurrency platforms. Its previous arsenal included traditional methods such as keylogging, fake login windows, and click interception. However, with the incorporation of UIA, Coyote has become far more sophisticated and insidious.
When a user opens a browser and navigates to a banking or exchange website, Coyote first attempts to identify the destination by examining the window title. If no match is found, it connects to the UIA automation tree, extracts URLs from tabs and the address bar, and compares them against a hardcoded list of 75 targeted services. These include Banco do Brasil, CaixaBank, Santander, Bradesco, as well as cryptocurrency services such as Binance, Electrum, Bitcoin, and Foxbit. If a match is detected, the surveillance module is activated.
The current phase of the attack appears to be limited to reconnaissance—monitoring the user interface to determine if a target site is open. However, Akamai researchers have demonstrated that the same mechanism can be used to intercept user input, including usernames and passwords. They published a technical proof-of-concept illustrating how UIA can be used to capture the contents of input fields, enabling full credential theft.
As of this writing, Microsoft has not issued any statements regarding potential restrictions or security enhancements to mitigate such misuse. The situation draws parallels with an enduring issue in the Android ecosystem, where accessibility services have long been exploited by malicious apps. In response, Google has steadily tightened its security policies for apps accessing Accessibility features.
Frameworks like UIA are created with benevolent intent—to empower individuals with special needs to interact with computers on equal footing. Yet as threat actors continue to explore increasingly unorthodox attack vectors, these powerful system mechanisms are becoming tools of choice in the arsenal of cybercrime.






