Image: ESET
The social engineering technique known as ClickFix—based on deceptive CAPTCHA prompts—has witnessed a dramatic surge in popularity among cybercriminals over the past year. According to ESET, between July 2024 and June 2025, the number of attacks leveraging ClickFix as an initial infection vector skyrocketed by an astonishing 517%.
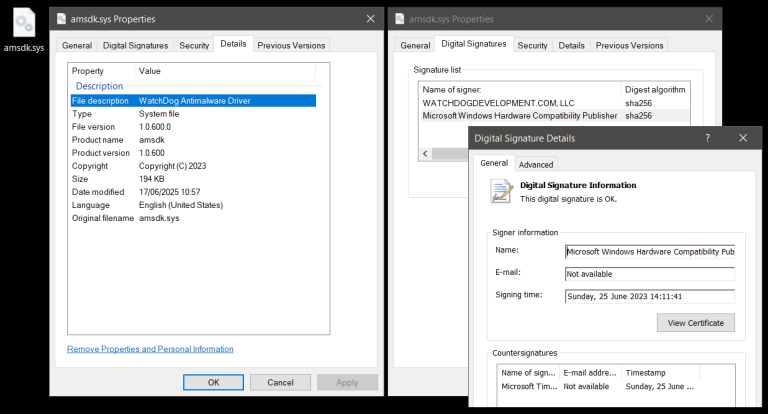
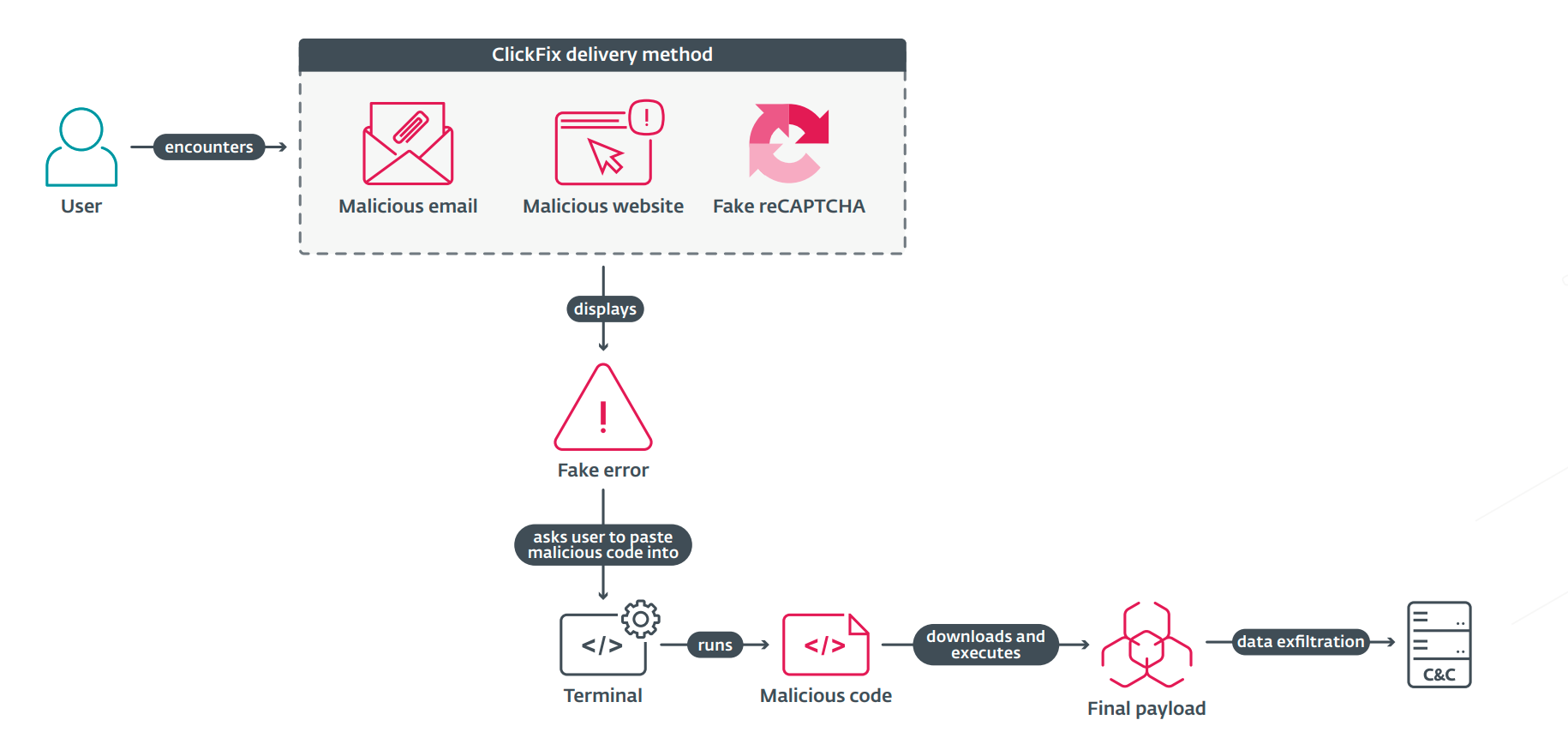
ClickFix is a deceptively simple yet remarkably effective method that coerces victims into unwittingly executing malicious code themselves. The target is presented with a counterfeit error message or a fraudulent CAPTCHA form, allegedly requiring verification. The user is then instructed to copy a provided text string and paste it either into the Windows “Run” dialog or into the macOS terminal—an action that ultimately triggers the execution of a dangerous script.
Security experts note that the range of threats disseminated through ClickFix continues to expand. These include spyware, ransomware, remote access trojans (RATs), cryptocurrency miners, post-exploitation tools, and even sophisticated malware strains developed by state-affiliated actors.
The highest levels of ClickFix activity have been recorded in Japan, Peru, Poland, Spain, and Slovakia itself. The method’s impressive effectiveness has given rise to dedicated toolkits, offering cybercriminals ready-to-use web pages embedded with ClickFix attack scripts.
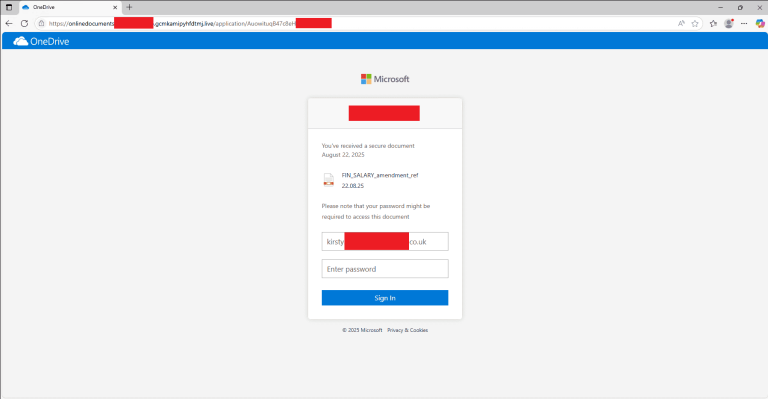
Simultaneously, another perilous technique has emerged—dubbed FileFix—demonstrated by the researcher known as mrd0x. Unlike ClickFix, which exploits the command line interface, FileFix takes advantage of the Windows File Explorer’s ability to execute system commands via the address bar.
A typical FileFix attack unfolds as follows: the victim is shown a fake webpage claiming the receipt of a document. The user is instructed to open File Explorer and paste a path copied from the clipboard. However, rather than a legitimate file path, the clipboard contains a concealed PowerShell command, masked by a decoy comment and whitespace to obscure the malicious payload. Once executed, the victim’s machine becomes compromised.
The rise of ClickFix and its derivatives underscores how even rudimentary social engineering tactics—when paired with technical flaws and psychological manipulation—remain alarmingly effective in the hands of adversaries.