SilentCrystal attack chain
The Trustwave SpiderLabs research team has documented a fresh wave of EncryptHub attacks, in which the human element and the exploitation of a Microsoft Management Console (MMC) vulnerability converge into a single, cohesive campaign. The operators impersonate technical support personnel, initiate contact via Microsoft Teams, persuade the “client” to grant remote access and execute a sequence of commands, and then deploy their payload by exploiting CVE-2025-26633—known as MSC EvilTwin. In parallel, the group leverages unconventional delivery channels, including the Brave Support platform, complicating traffic filtering and incident analysis. Also known under the aliases LARVA-208 and Water Gamayun, this group has previously been linked to attacks on Web3 developers and the abuse of the Steam platform. As of February, they had been tied to 618 compromised organizations worldwide.
The first stage is pure social engineering. The target receives a Teams message from a supposed IT staffer who insists on initiating a remote session to “check settings.” Once the session begins, the attacker executes a command resembling:
This retrieves and runs runner.ps1, which prepares the ground for exploiting the MMC flaw.
The next move is the twin .msc trick. The loader creates two identically named console files: a “clean” version in the expected directory and a malicious one in the MUIPath—commonly the en-US folder. When the legitimate snap-in launches, mmc.exe—due to the MSC EvilTwin flaw—prioritizes the MUIPath copy, executing the attacker’s code. Although publicly disclosed in March 2025, samples of such files had already been seen in February. A patch is available, but on unpatched machines the exploit remains effective.
Once the twins are deployed, runner.ps1 modifies the malicious snap-in by replacing the placeholder htmlLoaderUrl with the EncryptHub C2 address—e.g., hxxps://cjhsbam[.]com/payload/build[.]ps1. This fetches the next stage, build.ps1, which fingerprints the system, establishes persistence, maintains communications, and awaits tasks. Commands—AES-encrypted—are decrypted locally and executed via Invoke-Expression. Typical modules include the PowerShell-based Fickle Stealer, designed to exfiltrate sensitive files, environment details, and cryptocurrency wallet data.
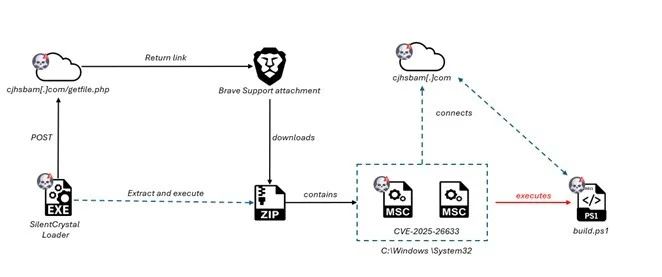
Investigators also identified Go-based tooling gradually replacing PowerShell scripts. One such loader, SilentCrystal, replicates the twin-.msc logic in a native binary. It first creates a deceptive system folder C:\Windows \System32 (note the space), visually mimicking the real path to mislead defenses. It then sends a POST request to the C2, embedding a hard-coded API key and a randomly named .zip file. In return, it receives a Brave Support link. Since regular accounts cannot upload attachments there, EncryptHub evidently maintains privileged access. The archive, once fetched and unpacked, replaces the {URI} placeholder in WF.msc with the C2 address; upon execution, the MSC EvilTwin flaw triggers again.
Another notable find is a Go-based SOCKS5 “proxy implant.” Without arguments, it runs in client mode, connecting to attacker-controlled hosting with hard-coded credentials, tunneling traffic. In server mode, it loads authentication data, generates a self-signed TLS certificate (Common Name: “Reverse Socks”; DNS: “localhost”), and listens for multiple concurrent connections via goroutines. Upon activation, it reports to a Telegram channel with the username, domain (USERDOMAIN), admin rights check result (net session), as well as public IP, geolocation, and ISP via https://ipinfo.io/json. Infrastructure analysis also revealed payload retrieval from hxxps://safesurf.fastdomain-uoemathhvq.workers.dev/payload/pay[.]ps1.
Beyond hosting on compromised assets, the group runs fake video-call services. One domain, api.rivatalk.net, links to a new C2. Registered in late July 2025 as a “platform” with Windows and web clients, RivaTalk requires an access code to download EXE/MSI installers—blocking casual researchers. Once the correct code is entered, setup.msi drops files including launcher.exe and a Symantec Early Launch Anti-Malware binary, abused to sideload a fake userenv.dll. This DLL executes:
The retrieved script displays a convincing “System Configuration” window to distract the victim, while in the background it schedules tasks to generate fake HTTP traffic to popular sites, masking C2 communications. It also collects the device UUID, maintains persistent C2 contact, and executes AES-wrapped commands via Invoke-Expression, granting full system control.
The campaign’s architecture is tightly integrated: a voice-phishing call, a Teams session, a one-liner PowerShell, twin .msc files with MUIPath redirection, a build.ps1 and Fickle Stealer duo, Go-based loaders and SOCKS5 tunnels, Brave Support abuse, and fake video calls—all crafted to bypass defenses, establish footholds, and operate under the guise of legitimate processes. A patch for CVE-2025-26633 is available, yet EncryptHub continues targeting unpatched systems and environments permitting unsigned script execution, where compromise remains likely.
Indicators of Compromise observed by SpiderLabs include:
rivatalk[.]net0daydreams[.]netcjhsbam[.]comsafesurf.fastdomain-uoemathhvq.workers[.]dev185.33.86.220
These overlap with the described infrastructure: Brave Support delivery links, a Cloudflare Workers C2 node for PowerShell distribution, and the RivaTalk “video platform” restricted to invitation-only downloads.






