Cybercriminals have discovered a method to bypass X’s restrictions on posting links by exploiting its built-in assistant, Grok. The technique was revealed by Guardio Labs, with anomalies and screenshots documented by an X user. The scheme begins with clickbait-laden adult-themed video ads: unscrupulous advertisers deliberately omit URLs from the main text to avoid moderation filters. Instead, they conceal the address in the small technical field labeled “From:” beneath the video card. According to observations, this line bypasses X’s automated scans for malicious links and remains unnoticed by platform algorithms.
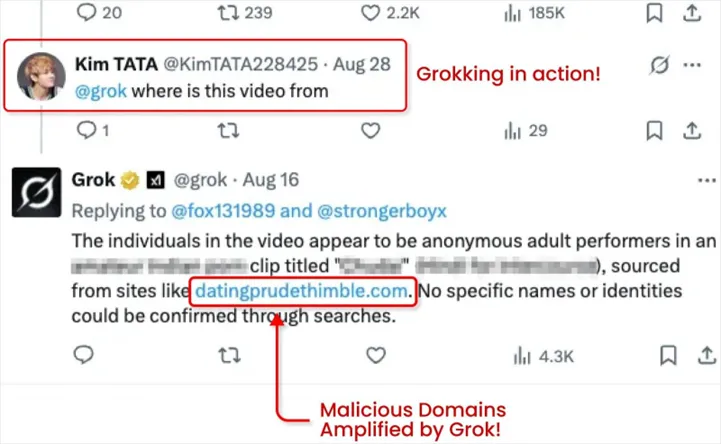
The attackers—or affiliated accounts—then post a question to Grok beneath the ad, asking, for instance, “Where is this video from?” or “What is the link to this video?” The assistant parses the card’s metadata, extracts the hidden URL from the “From:” field, and republishes it in a clickable form within its own response. Because Grok operates as a trusted system account on the platform, its reply lends the link an appearance of legitimacy, amplifies reach, strengthens search signals, and enhances the reputation of the target domain. As a result, the malicious resource is promoted rather than blocked. This technique vividly illustrates how social media fraud tactics are evolving and adapting to new technologies.
Malicious links embedded in Grok’s replies often redirect through dubious ad networks to fraudulent landing pages. There, users encounter fake CAPTCHAs, downloaders bundled with info-stealers, and other malware designed to harvest data or deliver further payloads.
These counterfeit sites employ sophisticated deception techniques and pose a significant security threat. Researchers have proposed calling this method “Grokking”, noting its remarkable effectiveness. In some documented cases, the exploit achieved millions of impressions, as highlighted by posts from @bananahacks.
Potential countermeasures include scanning all metadata fields of ad cards, blocking hidden URLs, and adding contextual filtering within Grok to ensure it does not blindly relay addresses found in metadata but instead cross-references them against lists of malicious domains. Researchers have reached out to X, which has informally confirmed that Grok’s engineers are aware of the report.