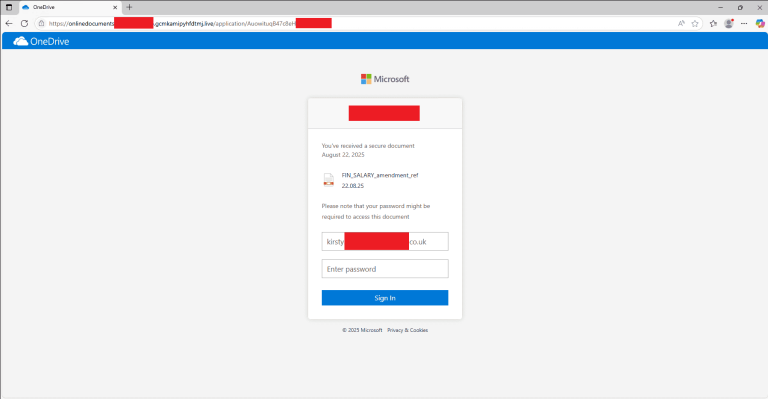
Vulnerable valid-signed WatchDog Antimalware Driver
The APT group Silver Fox has integrated a previously unknown vulnerable driver, WatchDog Antimalware, signed by Microsoft, into its attack chains. Exploiting this driver, the attackers disable defenses even on fully updated Windows 10 and 11 systems, paving the way for the seamless delivery of the ValleyRAT trojan.
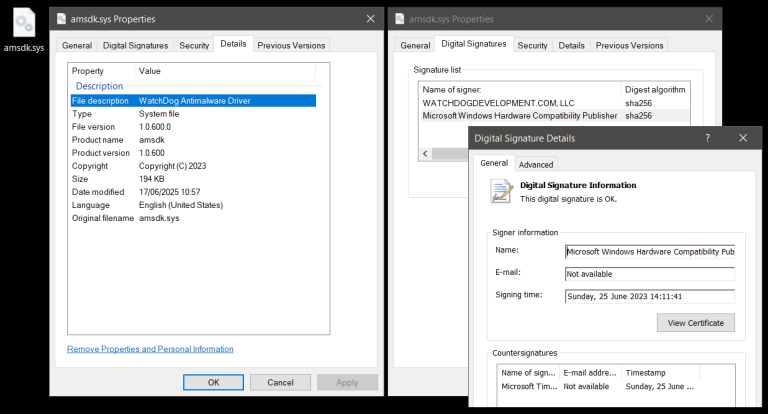
Researchers at Check Point Research documented an ongoing campaign leveraging the driver amsdk.sys v1.0.600—built on the Zemana Anti-Malware SDK. This driver is absent from Microsoft’s Vulnerable Driver Blocklist and unlisted in communities such as LOLDrivers. Although formally signed by Microsoft, the component enables adversaries to terminate processes protected by PP/PPL, thereby disabling even modern EDR and AV solutions without triggering signature-based detection. The attack employs a BYOVD scheme with a dual-driver loader: older systems rely on the known ZAM.exe from Zemana, while newer versions deploy the previously unidentified WatchDog driver. Both drivers are embedded within the loader, which also includes anti-analysis techniques, process-killing logic, and the ValleyRAT loader.
Following disclosure, the vendor released a patched driver (wamsdk.sys v1.1.100), eliminating the local privilege escalation flaw tied to DACL and FILE_DEVICE_SECURE_OPEN. However, the critical issue—arbitrary termination of processes, including PP/PPL—remained unresolved. Attackers swiftly adapted by modifying a single byte in the unauthenticated portion of the driver’s signature, allowing them to preserve Microsoft’s trust signature while bypassing hash-based blocking. This elegant evasion renders even newly patched drivers exploitable under the current validation model.
The ultimate payload across all observed samples remains ValleyRAT (Winos)—a modular RAT with infrastructure located in China. Each stage, from loader to backdoor, is implemented as a standalone 64-bit PE file, protected with UPX packing, anti-analysis techniques (Anti-VM, Anti-Sandbox, ISP/ORG filtering via ip-api.com), encoded strings (Base64 + hex), XOR encryption, and process injection into svchost.exe. Delivery occurs through .rar archives containing .exe or .dll files, injected via DLL Sideloading through legitimate applications. C2 server configurations are hardcoded, with IP addresses and ports stored in reverse order, including 156[.]234[.]58[.]194:52110 and :52111.
The anti-analysis tool (EDR/AV-killer) leverages two IOCTL commands: 0x80002010 registers its process in the allowlist, while 0x80002048 terminates targeted processes. The kill list includes 192 entries, primarily AV and EDR products widely used in China. Analysts also observed window-title checks for sandbox detection and delayed execution (via EnumWindows) when analysis environments are detected, bolstering resilience against investigation.
The root flaw in the WatchDog driver lies in its creation of a device with a “hard” DACL but without the FILE_DEVICE_SECURE_OPEN flag, enabling unrestricted access from any context. Additional vulnerabilities include local privilege escalation, arbitrary process termination, direct disk access (IOCTL_SCSI_READ/WRITE), and process handle hijacking (IOCTL_OPEN_PROCESS).
According to CPR, Silver Fox activity remains ongoing. Despite MSRC notification and partial blocking, campaigns now incorporate a modified wamsdk.sys version, derived from the patched driver but still exploitable. The digital signature remains valid since the alteration affects only portions not checked by the core validation process. This is a severe issue: the file passes all Windows trust verifications while evading signature-based blocking with a unique hash.
ValleyRAT continues to employ methods described in earlier research: in-memory execution, bypassing DllMain, stealthy background operations leaving no disk artifacts, and a modular architecture with remote configuration. It supports remote command execution, espionage, data exfiltration, and dynamic module loading. Researchers urge administrators to manually update Microsoft’s Vulnerable Driver Blocklist (which is infrequently refreshed by default), deploy custom YARA rules, and adopt behavioral detection mechanisms—since static signatures and even digital signature checks are no longer sufficient.