Analysts from FortiMail Workspace Security have uncovered a targeted campaign against Israeli companies and organizations within critical infrastructure sectors. The attackers exploited a compromised internal email system to send highly convincing messages to regional recipients. This wave initiated a multi-stage PowerShell-based infection chain without relying on any external executable files, ultimately delivering a Remote Access Trojan (RAT) that operated entirely within the scripting shell. Taken together, the indicators point to a high-risk threat: confirmed data exfiltration, covert surveillance, persistence within the environment, and lateral movement across networks.
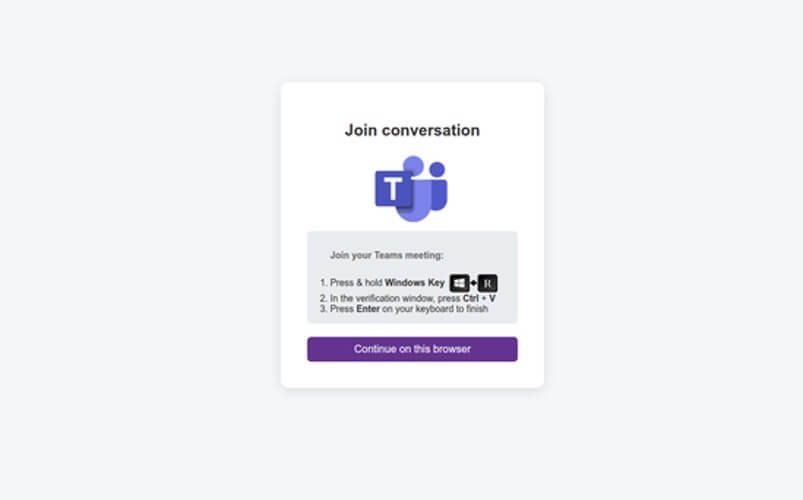
The lure posed as an invitation to a “mentorship meeting on procedures during military threats and the handling of medical and pharmaceutical supplies.” Recipients were encouraged to share the materials with colleagues, increasing internal reach. Clicking the embedded link led to a counterfeit Microsoft Teams page, faithfully imitating the interface and prompting the user to “Continue on this browser.” A subsequent prompt instructed them to press Windows+R, paste a lengthy string from the clipboard, and confirm with Enter — a social engineering trick designed to conceal the execution of a malicious PowerShell command via the Run dialog.
The phishing page’s markup contained a Base64 string split into three parts; when concatenated and decoded, it issued a command to download and execute a remote script:
This initiated a connection to the operator’s server and handed control to the next stage.
From the same host, two files were retrieved. First, test.html was saved to C:\Users\Public\Downloads\test.html via:
Inside was a blob containing a long string between <tag>…</tag> markers. Another network request —
— pulled a script that extracted the 11th line from test.html, isolated the content between the tags, split it by the delimiter kendrick, converted binary fragments into decimal values, then into characters, and finally reassembled and executed the payload with IEX. For example, kendrick1100110kendrick yields 1100110₂ = 102₁₀, corresponding to the letter f.
To accelerate analysis, researchers wrote a short Python decoder. The output was a compressed Base64 string in the form IEX (Decompress-Base64-String "...."). Decoding and decompressing the buffer produced PowerShell code, stored as a .ps1 file after passing through a GZip + Base64 unpacking function.
The network behavior was tightly bound to a single domain:
$global:SRV = "hxxps[:]//pharmacynod[.]com/"
Communication occurred over HTTPS. Immediately after launch, the malware registered the infected system (init), collecting environment parameters (Windows domain, hostname, account name), compressing them twice with GZip, encoding them in Base64, reversing the string, applying obfuscation, and sending it to /16625. It then entered an infinite loop with random 2–7 second pauses to simulate human activity. The Get-Appversion function polled the C2 via POST requests, receiving compressed and reversed instructions; Get-Decompress restored them to executable form.
Commands were mapped to numeric codes:
- 7979 — reinitialization, regenerating identifiers and refreshing the connection.
- 5322 — download a remote object and save to disk via
Get-FileusingSystem.Net.WebClient. - 4622 — adjust polling interval by updating
$time. - 2474 — execute arbitrary PowerShell commands, compressing and double-reversing output (including errors) before sending to
/17361.
This afforded the operator full RCE capability, module deployment, and data exfiltration.
Attribution remains inconclusive. In the observed incident, the adversary compromised Israeli companies in succession, using each breached site as a staging ground for further attacks — a tactic reminiscent of MuddyWater. However, notable deviations were present: deliberate avoidance of RMM tools and public file hosting, exclusive reliance on PowerShell, and the “ClickFix” initial vector instead of traditional droppers. The infrastructure, targeting, and scripting techniques mirror past episodes, yet the unique stage sequence leaves room for debate — either an evolved methodology or a different actor borrowing familiar tactics.
Stealth was achieved through multi-layered obfuscation and traffic masking. Payloads and C2 responses were encoded and compressed (double GZip, Base64, string reversal, + replaced with _ for URL compatibility). Transport used native .NET calls, realistic User-Agent headers via urlmon.dll, default credentials, and system proxy settings to blend with normal user traffic. The report also mapped each operational phase to the MITRE ATT&CK framework.
Fortinet solutions counter this attack on multiple fronts. FortiGuard Antivirus detects the family as PowerShell/Agent.PH!tr. FortiMail Workspace Security blocks the email delivery chain. FortiEDR stops malicious script execution, prevents memory injection, and detects RAT-like post-exploitation activity. FortiGate firewalls with IPS block C2 traffic and typical HTTPS beacons, while FortiGuard DNS/Web Filtering denies access to known malicious domains, including pharmacynod[.]com. FortiAnalyzer and FortiSIEM provide event correlation and visibility, and FortiNDR augments detection with behavioral analytics and ML, particularly for fileless or script-heavy intrusions. Threat databases are continuously updated by FortiGuard Labs; organizations suspecting compromise are advised to contact FortiGuard Incident Response.
Indicators of Compromise (IOCs) and key artifacts:
- Obfuscation: double GZip, Base64, string reversal,
+→_substitution. - C2 domain:
hxxps[:]//pharmacynod[.]com/ - Registration path:
/16625 - Command result endpoint:
/17361 - SHA-256 hash (PowerShell sample):
46a76b3c7851f30d68ebc6a5584bc099435b0544d8707fff7a9178f46046708b
Given the confirmed targeting of Israeli businesses and critical services, rapid detection of these patterns and prioritizing their remediation is essential for regional high-risk organizations.






