Researchers at Kaspersky Lab have reported the resurgence of ransomware operations by the group OldGremlin, which has once again begun targeting Russian companies. In the first half of 2025, eight major enterprises were compromised, primarily within the industrial sector. Additional victims included organizations in healthcare, retail, and IT.
OldGremlin was first identified five years ago and is notorious for its sophisticated techniques and prolonged stealth within victim networks—remaining undetected for an average of 49 days before deploying ransomware. The group was particularly active between 2020 and 2022 and was last mentioned in 2024. In the past, its demands reached staggering sums, including nearly $17 million in a single incident.
In its 2025 campaigns, OldGremlin introduced an updated toolset. The attackers exploited a vulnerability in a legitimate driver to disable security solutions on infected machines and abused the official Node.js runtime to execute malicious scripts. Their ransom notes carried a modified name, OldGremlins, a variation first seen in prior research publications.
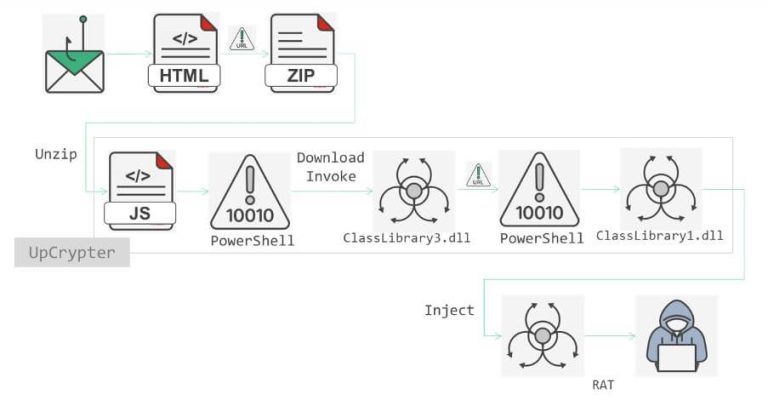
The attacks typically began with phishing emails, which delivered a backdoor enabling remote control over compromised systems. From there, the driver vulnerability was leveraged to disable Windows defenses, allowing the deployment of a custom encryption driver.
The updated malware not only encrypted files but also relayed infection status updates back to the attackers. The final phase included leaving a ransom note, erasing traces of malicious activity, and temporarily disconnecting the device from the network—measures designed to complicate forensic investigation.
According to researchers, OldGremlin’s return in 2025 was marked by improved tooling and a more overt declaration of its presence. By openly adopting the name assigned to them by the security community, the group signaled its intent to continue operations.
The malware observed in these attacks has been classified as Trojan-Ransom.Win64.OldGremlin, Backdoor.JS.Agent.og, HEUR:Trojan.JS.Starter.og, and HEUR:Trojan-Ransom.Win64.Generic.
Experts stress that to mitigate such risks, companies must regularly update software, monitor for anomalies in outbound traffic, and maintain offline backups of critical data. Equally crucial is ensuring that security teams have access to the most current intelligence on adversaries’ tactics and techniques.