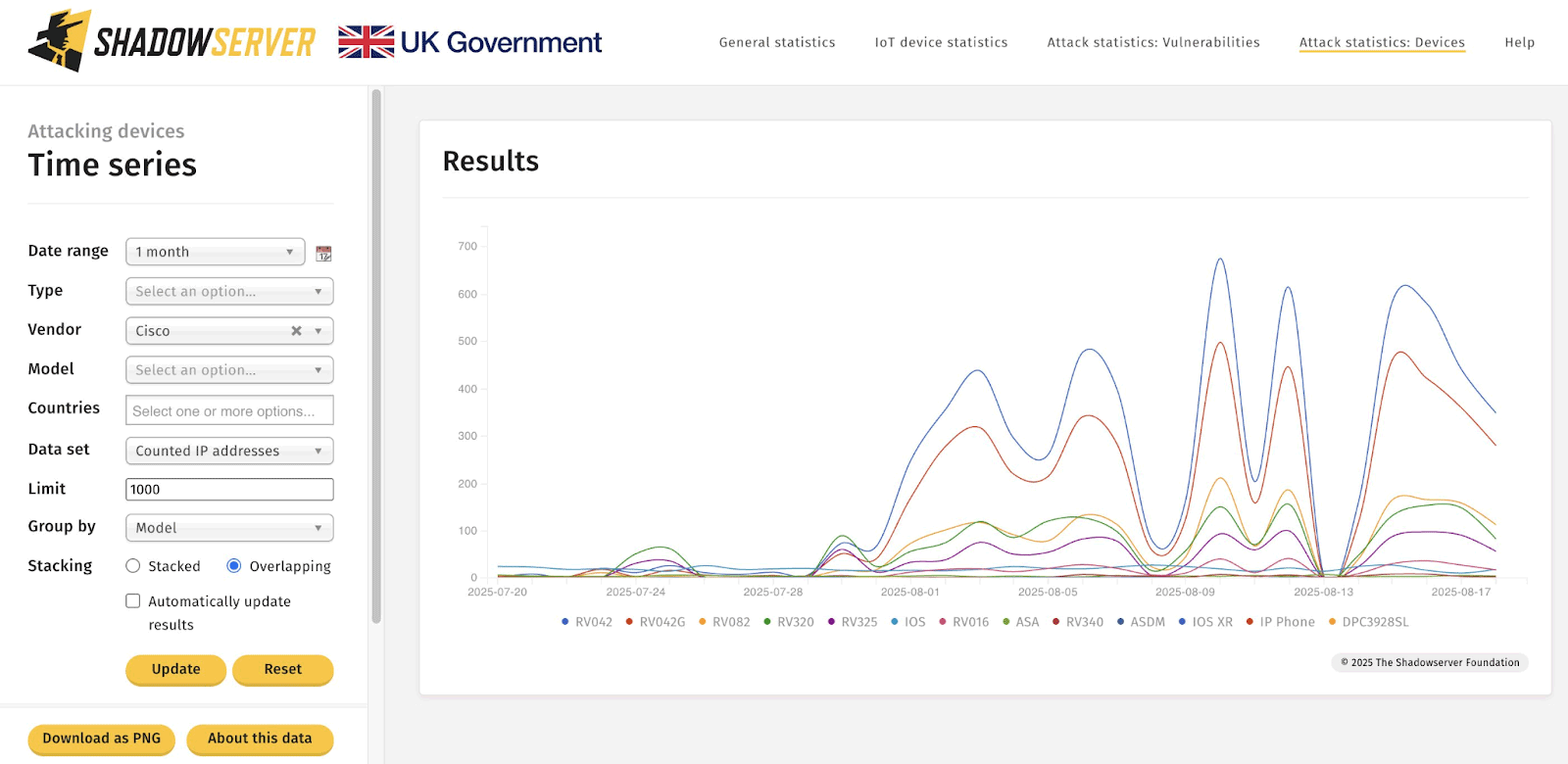
Uptick in scans from select IoT devices. (Credit: Shadowserver Foundation)
Researchers at Eclypsium have recorded a sharp increase in scanning activity targeting outdated and long-abandoned network equipment. The chief danger lies in the fact that many of these attacks are being launched from already-compromised devices manufactured by Cisco, Linksys, and Araknis—all of which have been out of support for years and no longer receive updates. According to the Shadowserver Foundation, the number of newly compromised routers has exceeded 2,200 in recent months, and the figure continues to climb.
The Eclypsium report emphasizes that attackers care little whether they exploit modern vulnerabilities or flaws that are more than 15 years old—what matters is that the device remains exposed. Among the models most aggressively targeted are Cisco Small Business RV routers, which are fully end-of-life; the Linksys LRT series, which now receives only limited patches; and the Araknis Networks AN-300-RT-4L2W, for which firmware updates are no longer available. These devices still operate in corporate infrastructure and home networks but in practice serve as wide-open gateways for intrusion.
The threat is compounded by legacy protocols inherited from older generations of network software. The FBI has previously warned that attackers actively exploit mechanisms such as Cisco Smart Install (SMI) and SNMP, both of which transmit data without encryption. Even though CVE-2018-0171 has been public for seven years, it continues to provide threat actors with reliable means of compromise. And even when patches are released, many users are slow to apply them—while small businesses and private owners often ignore updates altogether, making the issue a chronic one.
Researchers describe these neglected corners of IT infrastructure—obsolete hardware, legacy Windows systems tied to closed applications, and forgotten services without updates—as “dusty corners” that remain potential entry points. In such conditions, cybercriminals need only launch broad internet scans to locate and infect vulnerable devices.
Currently, the Huawei Home Gateway HG532 routers have become the most frequent targets. Nearly 600 unique IP addresses strike Shadowserver honeypots daily, attempting to exploit a critical remote vulnerability discovered back in 2017, which enables attackers to gain full device control by sending specially crafted packets.
Next in popularity are attacks against SonicWall firewalls. Adversaries continue to hunt for a 2022 SonicOS flaw enabling denial-of-service or code execution without authentication, as well as a 2023 bug that can disable security appliances entirely. On average, around 300 unique IPs test for these weaknesses every day.
Hundreds of traffic sources also continue scanning for vulnerabilities in Cisco IOS XE disclosed in 2018 and 2023, exploiting a 2019 Belkin Wemo flaw, leveraging a decade-old Realtek SDK bug, and abusing long-known security issues in the Zyxel Eir D1000 dating back to 2016.
Experts stress that the only truly effective way to mitigate such risks is to abandon legacy protocols like TELNET, SNMP, and SMI, replace hardware that is no longer maintained, and ensure all systems remain up to date—even those that seem secondary. It is especially critical to regularly update router and Wi-Fi access point firmware, as these devices often serve as the first targets for attackers.