Mandiant researchers have uncovered an attack targeting legacy installations of the Sitecore platform. The attackers exploited a demonstration ASP.NET key that had been publicly included in official documentation until 2017. This flaw, tracked as CVE-2025-53690, enables remote code execution through the deserialization mechanism of ViewState.
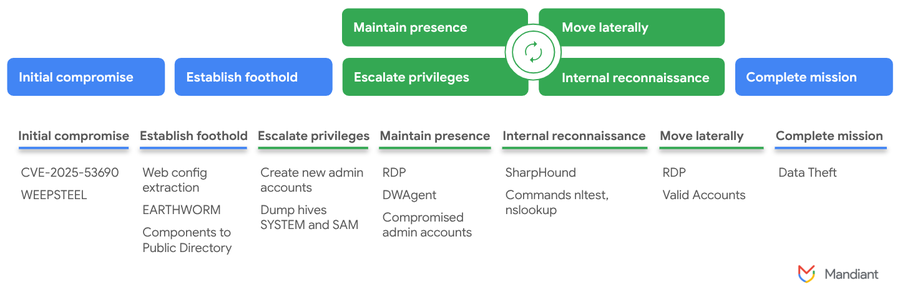
The attack began with a simple request to the /sitecore/blocked.aspx page, which exists in every Sitecore installation. This page requires no authentication and contains a hidden ViewState field—an ideal entry point for injecting malicious code. Threat actors submitted crafted POST requests with a ViewState payload signed using the outdated machineKey from the documentation. Although newer Sitecore versions no longer rely on such keys, many older deployments remain exposed.
Once access was gained, the attackers uploaded a .NET library named Information.dll (known as WEEPSTEEL). This reconnaissance tool collected details such as the operating system version, network configuration, active processes, and the structure of the web application. All harvested data was exfiltrated through the same ViewState field, disguised as a legitimate server response.
The attackers then archived the entire website root directory, including the critical web.config file containing server settings. They executed system commands to enumerate users, processes, network connections, and domain structure. To establish persistence, they leveraged three open-source tools: EARTHWORM (a tunneling server with SOCKS proxy), DWAGENT (remote management with SYSTEM privileges), and SHARPHOUND (Active Directory data collection).
At the next stage, two fake administrator accounts—asp$ and sawadmin—were created, camouflaged as regular system users. With administrative privileges, the attackers extracted SAM and SYSTEM registry hives to obtain password hashes. They also deployed GoToken.exe to hijack and reuse user authentication tokens.
For remote access, the adversaries used RDP, routing traffic through the EARTHWORM proxy. This allowed them to upload additional tools, including scripts and remote administration clients. Simultaneously, they conducted domain reconnaissance, hunting for weak passwords in Group Policy XML files.
In the final stage, the temporary accounts asp$ and sawadmin were removed, and operations were carried out under legitimate domain administrator identities. To compromise further machines, the attackers again relied on RDP, deploying EARTHWORM tunnels and system auditing utilities.
Although the intrusion was contained relatively early, Mandiant emphasized the attackers’ high level of expertise. They demonstrated a thorough understanding of Sitecore’s architecture and the intricacies of ViewState. Every step—from initial access to persistence and lateral movement—was carefully orchestrated.
Administrators of Sitecore XP versions prior to 9.0 and the Active Directory module prior to 1.4 must urgently:
- Replace default
<machineKey>values in web.config with unique keys. - Enable MAC validation for ViewState.
- Encrypt sensitive configuration parameters.
Environments with identical keys across multiple servers are at particular risk. Vulnerable products include Sitecore Experience Manager, Experience Platform, Experience Commerce, and Managed Cloud. Safe from this flaw are XM Cloud, Content Hub, CDP, Personalize, OrderCloud, Send, Discover, Search, and Commerce Server.
Mandiant has published a full set of indicators of compromise (IOCs) in its GTI collection, including IP addresses, malicious file hashes, and compromised account names. Administrators are urged to follow official security guidance and ensure the regular rotation of ASP.NET keys.