Mexican organizations remain the persistent targets of an enduring cybercriminal campaign involving modified versions of the AllaKore RAT and SystemBC malware. According to analysts at Arctic Wolf Labs, the attacks are orchestrated by a financially motivated threat actor known as Greedy Sponge, which has been active since early 2021.
Over the past four years, this group has targeted a wide array of victims—from agricultural and banking enterprises to the transportation sector, entertainment industry, and government entities. Despite this broad reach, their operations remain geographically focused, with Mexico serving as the primary theatre. Researchers believe the campaign’s longevity and minimal infrastructure changes underscore its operational success.
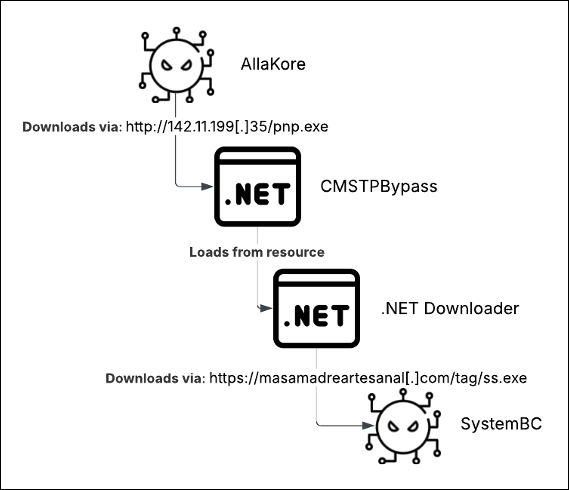
At the core of the attacks lies a meticulously enhanced version of AllaKore RAT—a remote access trojan capable of keylogging, screen capture, file upload/download, and now, harvesting banking credentials and unique authentication data, which is exfiltrated to a remote server for fraudulent use.
The first comprehensive account of the campaign surfaced in January 2024, through the efforts of BlackBerry’s threat intelligence team, now part of Arctic Wolf. According to their findings, initial infection vectors typically involve phishing emails or ZIP archives delivered via malicious links. One such archive, named “Actualiza_Policy_v01.zip,” contains a legitimate Chrome Proxy executable alongside a trojanized MSI installer masquerading as benign software.
This MSI file leverages a built-in .NET loader to fetch its payload from a remote server (manzisuape[.]com/amw), while invoking a PowerShell script to erase forensic traces. Upon installation, AllaKore RAT activates and, if required, downloads additional payloads such as SystemBC—a malware that transforms the compromised host into a SOCKS5 proxy node, granting attackers covert access to internal systems and command-and-control (C2) infrastructure.
Since mid-2024, the campaign has incorporated more advanced geofiltering. Previously, region-based restrictions (targeting Mexico) were enforced client-side within the .NET loader embedded in the MSI. This mechanism has since migrated to the server side, significantly complicating external threat analysis.
These attacks unfold alongside other active threats. In May 2025, eSentire reported a phishing campaign leveraging a novel malware obfuscation service dubbed Ghost Crypt. This malware was concealed in a PDF file containing a link to a Zoho WorkDrive folder housing an encrypted PureRAT loader. Victims were enticed to open the file, which then deployed a “process hollowing” technique to inject a DLL into the Windows process csc.exe.
First observed on underground forums in April 2025, Ghost Crypt is designed to evade Microsoft Defender and is compatible with a wide spectrum of malware—from infostealers (Lumma, StealC, Rhadamanthys) to loaders and remote access trojans (XWorm, DCRat, BlueLoader, and others).
Additionally, a new variant of Neptune RAT (also known as MasonRAT) has emerged, distributed via JavaScript-based lures. This malware is capable of extracting sensitive data, recording keystrokes, capturing screenshots, installing clipboard hijackers, and loading auxiliary DLL modules.
Similar attack chains have been observed involving Inno Setup-based droppers. These initiate Hijack Loader (aka IDAT Loader), which then deploys RedLine Stealer—a tool for exfiltrating user data. According to Splunk researchers, this method closely mirrors the tactics of the previously widespread D3F@ck Loader, including the use of Pascal scripts to execute payloads.
The sustained operations of Greedy Sponge illustrate not only tactical resilience and predictability but also the efficacy of minor malware and infrastructure tweaks in evading detection over extended periods. Within this context, Mexico emerges as a de facto testing ground where financially motivated cybercrime thrives with alarming ease—and, most concerningly, faces little meaningful resistance.






