Bitdefender researchers have identified a previously unknown cyber-espionage group, provisionally dubbed Curly COMrades. According to the report, the threat actors are focused on maintaining long-term, covert access to the infrastructure of Georgian governmental and judicial institutions, as well as to an energy enterprise in Moldova.
Among their primary activities were repeated attempts to exfiltrate the NTDS database from domain controllers—containing password hashes and authentication data—as well as the dumping of LSASS process memory to obtain credentials, potentially including plaintext user passwords. The initial intrusion vector remains unknown.
Curly COMrades’ activity has been tracked since mid-2024, yet the earliest signs of their custom malware, MucorAgent, date back to November 2023, suggesting operations may have begun earlier.
The name Curly COMrades derives from their extensive use of the curl utility for C2 communications and data exfiltration, alongside their exploitation of COM (Component Object Model) hijacking techniques. Other hallmarks include stealth, a methodical approach, and resilient infrastructure—leveraging repeated attempts, redundant methods, and incremental configuration to minimize noise and evade detection.
To maintain persistence, the group deployed MucorAgent via COM hijacking using a CLSID associated with the .NET Framework’s Native Image Generator (Ngen) service. Although the related scheduled task is marked as disabled, the operating system may still execute it spontaneously—during idle periods or new application installations—making it an ideal mechanism for quietly restoring access.
MucorAgent is a modular .NET implant deployed in three stages. It can decrypt and execute PowerShell scripts, uploading their output to a C2 server. Bitdefender notes that each encrypted script is erased from memory after execution, and no persistent channel for delivering new payloads was found—indicating its role as a tool for periodic access rather than constant presence.
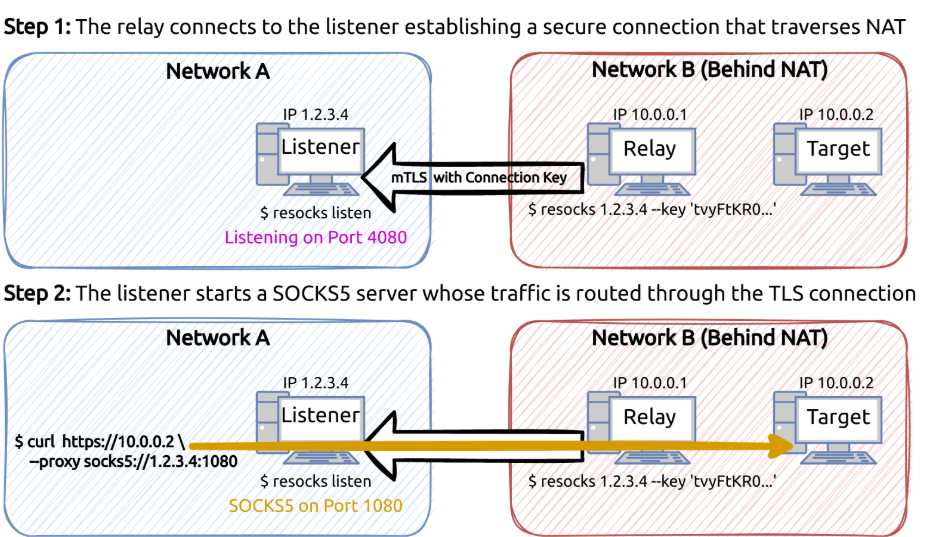
The group made extensive use of legitimate utilities to disguise their traffic: Resocks, SSH, Stunnel, and SOCKS5, as well as tools such as CurlCat (STDIN/STDOUT redirection over HTTPS), RuRat (a legitimate remote administration tool), Mimikatz (for credential extraction), built-in Windows commands (netstat, tasklist, systeminfo, ipconfig, ping), and PowerShell scripts with curl for data exfiltration.
Notably, they used compromised but otherwise legitimate websites for C2 communications and data leakage, allowing them to operate without raising suspicion. This demonstrates both high adaptability and a strong focus on stealth.
Bitdefender emphasizes that Curly COMrades do not rely on zero-day vulnerabilities. Instead, they favor publicly available utilities, open-source projects, and so-called LOLBins (Living-off-the-Land Binaries), tailoring common techniques to each target’s environment. This makes them a highly flexible and difficult-to-detect adversary, intent on maintaining a prolonged presence within compromised networks.




