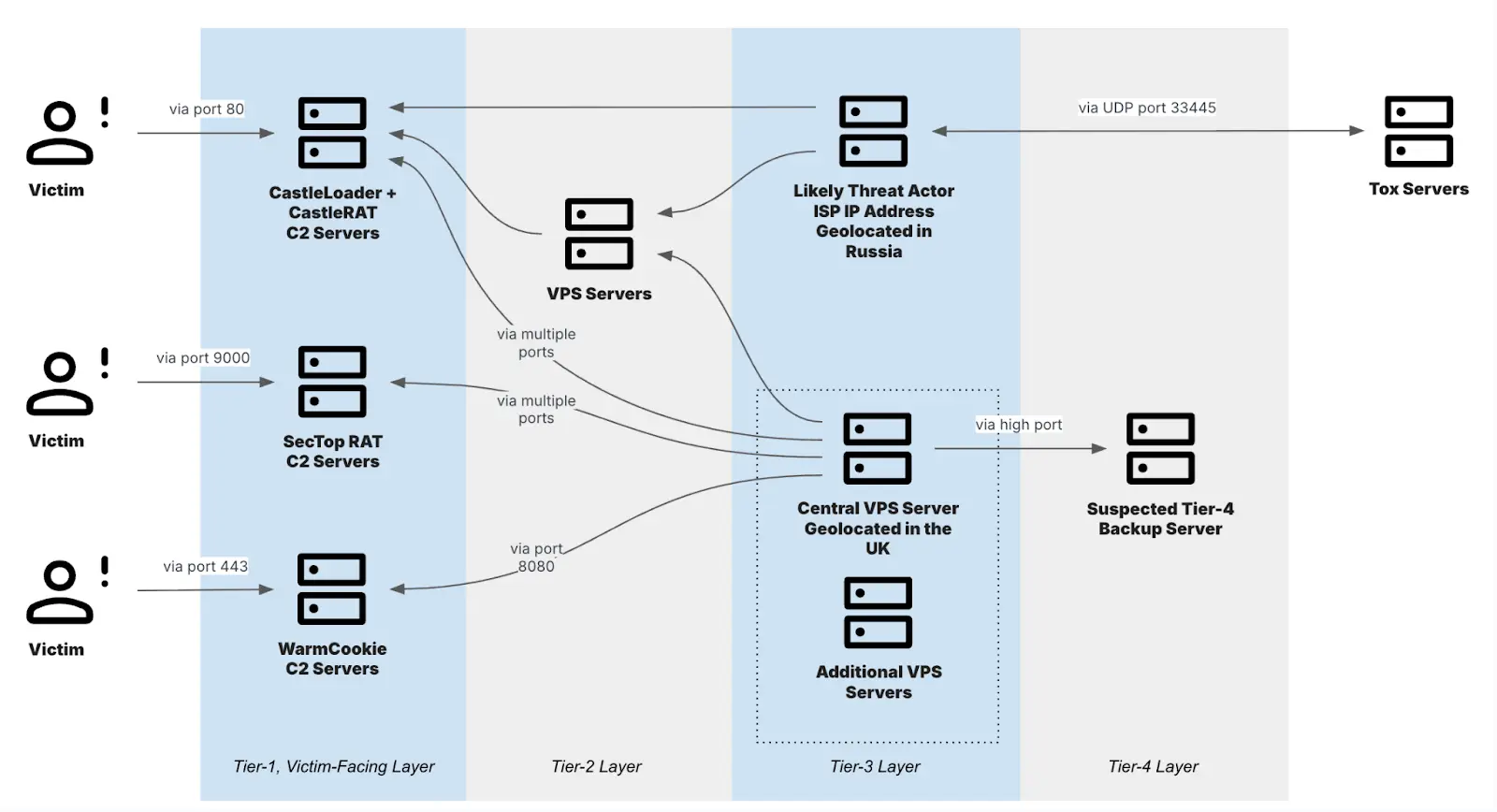
Multi-tiered infrastructure linked to TAG-150 (Source: Recorded Future)
The threat group TAG-150, which researchers associate with the development of the CastleLoader malware, has expanded its arsenal with a new remote access trojan (RAT) known as CastleRAT. The discovery was reported by Recorded Future’s Insikt Group, which noted that the malware exists in two variants — one written in Python and the other in C.
CastleRAT is capable of harvesting system information, downloading and executing additional modules, and issuing commands through CMD and PowerShell. The Python version, also referred to as PyNightshade, offers basic capabilities, while the C-based variant provides a more extensive toolkit. It can log keystrokes, capture screenshots, upload and download files, and even act as a cryptocurrency clipper, replacing copied wallet addresses with those controlled by attackers. To gather victim information, both versions query ip-api[.]com for public IP data. Earlier builds of the C version also collected geolocation details such as city and postal code, as well as indicators of VPN, proxy, or TOR use — functionality that has since been partially removed, indicating ongoing active development.
According to Recorded Future, TAG-150 has been active since at least March 2025. CastleLoader, first documented by PRODAFT in July of the same year, has been used to deliver multiple secondary payloads, including DeerStealer, RedLine, StealC, NetSupport RAT, SectopRAT, and Hijack Loader. Later, IBM X-Force observed that it was also distributing MonsterV2 and WARMCOOKIE, typically delivered through SEO poisoning and fake GitHub repositories impersonating legitimate software.
Initial infection vectors often involve phishing campaigns masquerading as Cloudflare using the ClickFix technique, or fraudulent GitHub projects. ClickFix campaigns exploit domains disguised as developer libraries, video conferencing platforms, fake “browser update” notices, and document verification services.
TAG-150’s infrastructure is layered: Tier 1 consists of C2 servers communicating directly with victims, Tiers 2 and 3 are mostly virtual private servers, while Tier 4 serves as backup nodes. CastleRAT also leverages covert communication channels — researchers identified the use of Steam Community profiles as “dead drops” for delivering C2 addresses, one of which resolved to programsbookss[.]com.
Canadian cybersecurity firm eSentire, which analyzed the same tool under the name NightshadeC2, described it as a botnet delivered via a .NET-based loader. This loader employs advanced Windows defense evasion techniques, including UAC prompt bombing. When executed, the loader repeatedly attempts to add the final payload as an exclusion in Windows Defender via PowerShell. If successful, the malware is deployed; if not, the endless UAC loop disrupts execution and hinders sandbox analysis.
Further, some NightshadeC2 builds include modules to extract passwords and cookies from Chromium- and Gecko-based browsers, significantly increasing its data theft potential.
The discovery of CastleRAT coincides with reports of other new loaders and trojans. Hunt.io documented TinyLoader, a tool used to install RedLine Stealer and DCRat. TinyLoader achieves persistence through Windows registry modifications, monitors the clipboard for cryptocurrency addresses, and instantly swaps them for attacker-controlled ones. Its command-and-control panels are hosted on servers in Latvia, the UK, and the Netherlands, and it propagates via infected USB drives, network shares, and malicious shortcuts.
Two additional threats have also been observed:
- TinkyWinkey, a Windows keylogger that maintains persistence via system services, deploys low-level key interceptors, and collects detailed system data.
- Inf0s3c Stealer, a Python-based infostealer that harvests host information, CPU and network details, captures screenshots, inspects running processes, and enumerates user directories such as Desktop, Documents, Pictures, and Downloads. Its analysis revealed similarities to public projects like Blank Grabber and Umbral-Stealer, suggesting a shared lineage.
Taken together, these findings underscore the rapid expansion of the Malware-as-a-Service (MaaS) ecosystem. CastleLoader and CastleRAT form the backbone of a growing wave of attacks, enabling the distribution of stealers, RATs, and additional loaders. Simultaneously, emerging threats such as TinyLoader, TinkyWinkey, and Inf0s3c Stealer highlight the accelerating innovation and diversification of the underground cybercrime market.






