Between June and July 2025, researchers recorded hundreds of thousands of password brute-force attempts targeting SSL VPN and RDP services. The source of the attacks was traced to the Ukrainian autonomous system FDN3 (AS211736), registered to FOP Dmytro Nedilskyi. Each campaign lasted up to three days and focused on attempts to infiltrate corporate networks.
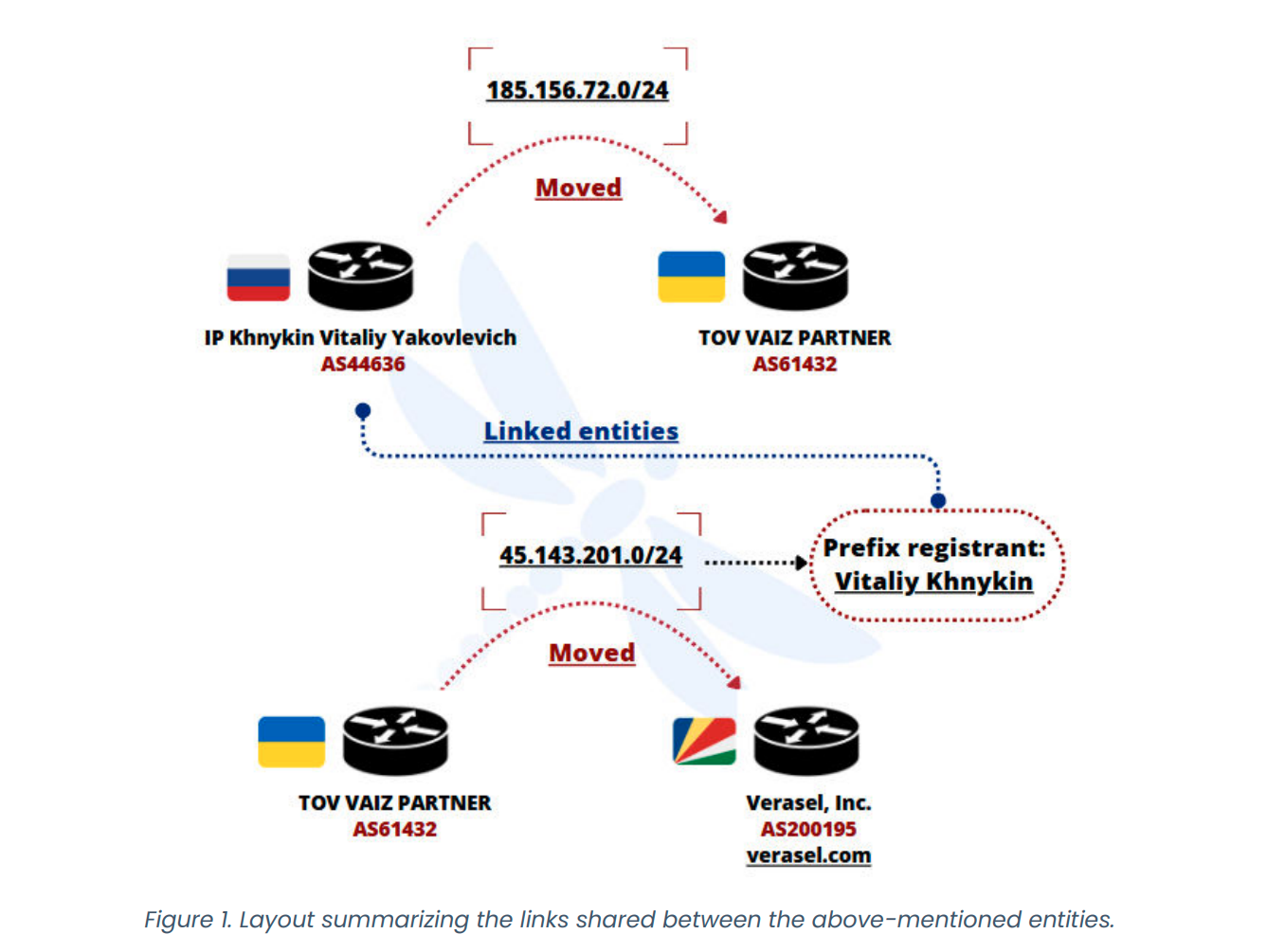
FDN3 forms part of a broader criminal infrastructure, which also includes the Ukrainian networks VAIZ-AS (AS61432) and ERISHENNYA-ASN (AS210950), along with the Seychelles-registered TK-NET (AS210848). All of these emerged in August 2021 and have since routinely exchanged IPv4 prefixes to circumvent blocking measures and continue hosting malicious services.
The report also highlights persistent links with other criminal operators. Chief among them is Ecatel in the Seychelles—operating under IP Volume Inc. (AS202425)—which became the primary transit provider for FDN3 and its partners. Similar attacks were launched through this network during the same periods. Evidence also points to cooperation with Virtualine, a hosting provider managing the U.S.-based network KPROHOST LLC (AS214940), which likewise exchanged prefixes with FDN3.
Despite redeclaring prefixes through new channels, the attack patterns remained unchanged, suggesting that the entire infrastructure may be centrally managed by a single administrator, merely reshaping its outer shell to evade takedowns and complicate attribution.
The study was conducted by Intrinsec, leveraging its Cyber Threat Intelligence division. The team collected data through proprietary monitoring and incident response services, alongside custom honeypot systems and reverse engineering. Their assessment concludes that the growing volume of such campaigns and the increasingly intricate ties between groups demand proactive defense measures: early detection of suspicious activity, continuous security updates, and the use of external intelligence for timely response.
Analysts emphasize that these attacks starkly illustrate how resilient criminal infrastructures have become—and how tightly they interconnect, ensuring both anonymity and the uninterrupted continuity of their operations.