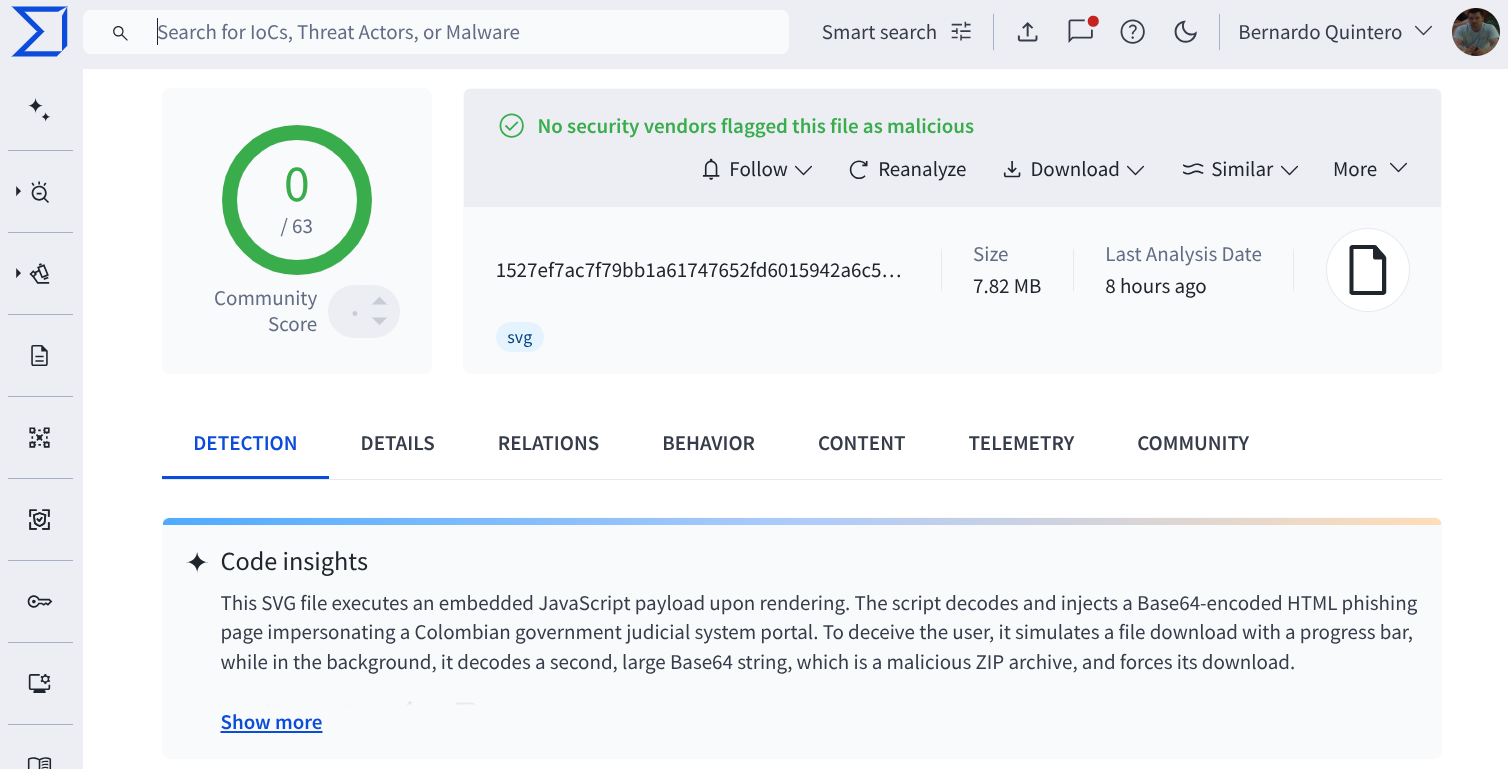
Cybercriminals have launched a new wave of attacks that employ SVG files as carriers for phishing pages. According to researchers at VirusTotal, the attackers disguise themselves as representatives of the Colombian Prosecutor’s Office, distributing email attachments containing hidden JavaScript. Automated analysis revealed behaviors that antivirus engines failed to detect.
Meanwhile, SWF files—a format considered obsolete since the deprecation of Flash in 2020—continue to surface in traffic. Over the course of 30 days, VirusTotal received 47,812 previously unseen unique SWF samples, 466 of which triggered detections by at least one antivirus engine. In one case, only 3 out of 63 scanners flagged suspicious traits and an old vulnerability, yet deeper inspection revealed a complex structure involving 3D rendering, audio, and an embedded level editor. Obfuscated classes, use of RC4/AES encryption, and system data collection appeared suspicious but ultimately aligned with anti-cheat and anti-modification logic. No malicious behavior was confirmed.
SVG, however, represents the opposite end of the spectrum: an open standard for the web and design, and precisely for that reason, a prime choice for attackers. In the past 30 days alone, VirusTotal processed 140,803 unique SVG files, of which 1,442 raised at least one detection. One notable sample slipped past every engine undetected but, upon rendering, executed an embedded script that decoded and injected a phishing HTML page mimicking the Colombian judicial portal. To appear legitimate, the page simulated document loading with a progress bar while, in the background, a ZIP archive was fetched and forcefully offered for download. Sandbox analysis confirmed the deception: visual elements, case numbers, and “security tokens” were all present—yet it was nothing more than an SVG image.
VirusTotal data indicates this is far from an isolated case. A query for type:svg mentioning Colombia uncovered 44 unique SVG files, none flagged by antivirus products, yet all employing the same tactics: obfuscation, polymorphism, and voluminous “junk” code to increase entropy. Embedded in the scripts were Spanish-language comments such as “POLIFORMISMO_MASIVO_SEGURO” and “Funciones dummy MASIVAS”—a clear weakness that could be leveraged for straightforward YARA signatures.
A year-long search revealed 523 matches. The earliest, dated August 14, 2025, also originated from Colombia and initially evaded detection. Follow-up analysis confirmed the same phishing and hidden download scheme. Early samples were bulkier, around 25 MB, but later shrank in size, suggesting refinements to the payload. The delivery channel remained email, with metadata on senders, subject lines, and attachment names linking the campaign into a consistent chain of activity.





