On underground forums, cybercriminals have claimed they have begun deploying HexStrike AI—a new open-source penetration testing tool—against Citrix NetScaler vulnerabilities just hours after they were publicly disclosed. The news was reported by Check Point evangelist Amit Weigman, who emphasized that the window between the publication of vulnerabilities and their mass exploitation is shrinking at an alarming pace.
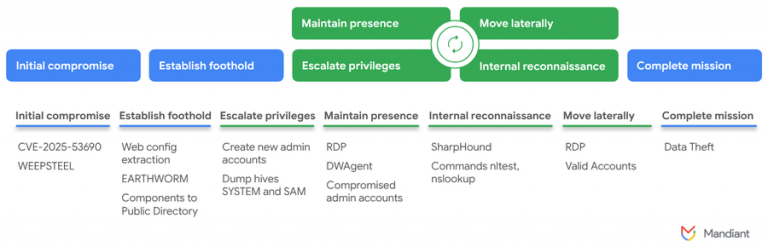
At the center of the storm lies CVE-2025-7775, a critical flaw enabling unauthenticated remote code execution. It was weaponized as a zero-day, with attackers implanting web shells and backdoors into devices even before Citrix had released a patch. Weigman warns that with HexStrike AI in circulation, the scale of attacks is set to surge in the coming days.
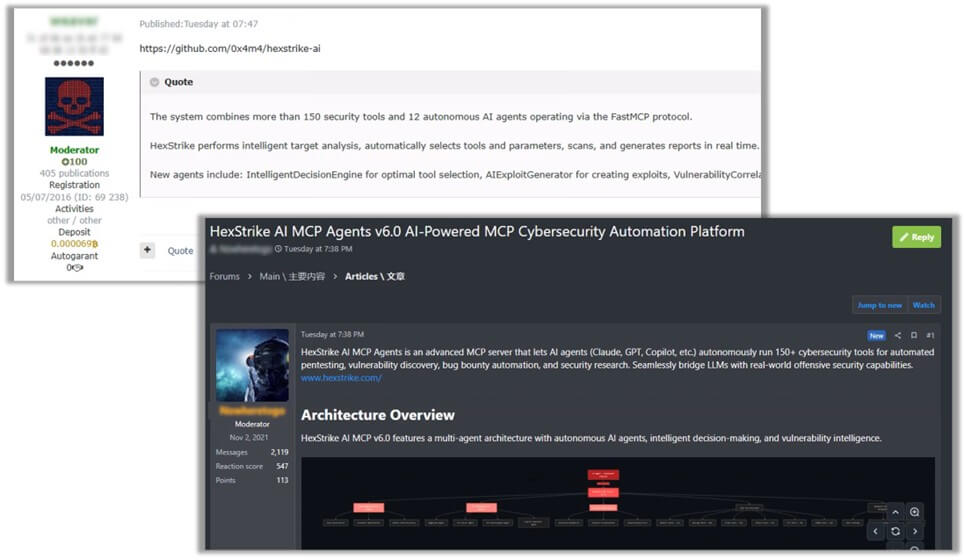
HexStrike AI was developed by security researcher Muhammad Osama, who uploaded the project to GitHub only weeks ago. Marketed as an AI-powered framework for penetration testing, it integrates with more than 150 tools spanning network scanning, web application analysis, reverse engineering, and more. It also connects to dozens of AI-driven agents designed to hunt vulnerabilities, automate exploit creation, and orchestrate novel attack chains.
The GitHub repository explicitly prohibits unauthorized testing, data theft, or any form of illegal activity. Nevertheless, almost immediately after its release, dark web discussions surfaced on how to repurpose HexStrike AI for exploiting Citrix NetScaler flaws. According to Check Point, within just twelve hours of CVE-2025-7775’s disclosure, threat actors were already boasting about using it to generate exploits and scan for vulnerable NetScaler instances.
Previously, such campaigns were considered the domain of seasoned specialists, requiring deep knowledge of memory exploitation, authentication bypass techniques, and NetScaler’s architecture—often weeks of preparation. Now, as Check Point security architect Aaron Rose notes, AI drastically lowers the barrier: these attacks can be automated in minutes, enabling wide-scale campaigns at a speed defensive systems are ill-prepared to counter.
Although Check Point has yet to confirm successful exploitation using HexStrike AI, analysts see troubling signs in criminal communities. Rose predicts that verifiable cases will emerge in the near future.
Osama, the tool’s creator, insists that HexStrike AI was built for defenders. His stated goal is to accelerate penetration testing and resilience assessments through automation and neural networks. He stresses that the framework does not ship with ready-made zero-day exploits; rather, it orchestrates workflows and allows users to integrate their own logic. He has deliberately withheld a RAG (Retrieval-Augmented Generation) version, which could dynamically ingest CVE data and reconfigure testing scenarios in real time.
RAG—where large language models are combined with search systems—produces more precise, context-aware results. Osama argues that the mission of HexStrike is to give defenders the same adaptive capabilities attackers are already leveraging. In his view, the future of cybersecurity lies in AI-driven orchestration and autonomous agents, capable of shaping both offensive and defensive strategies alike.