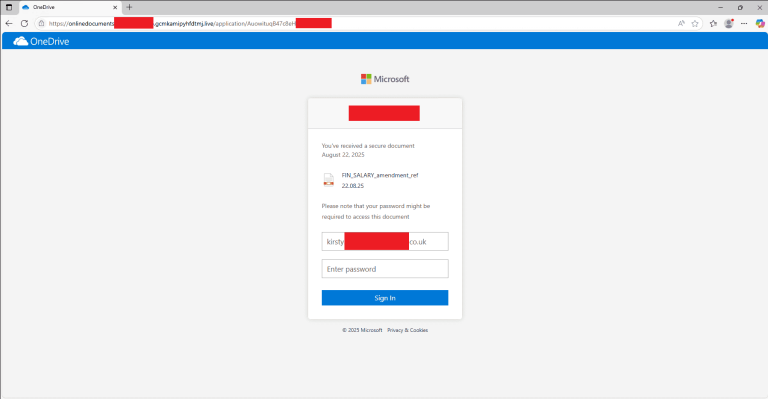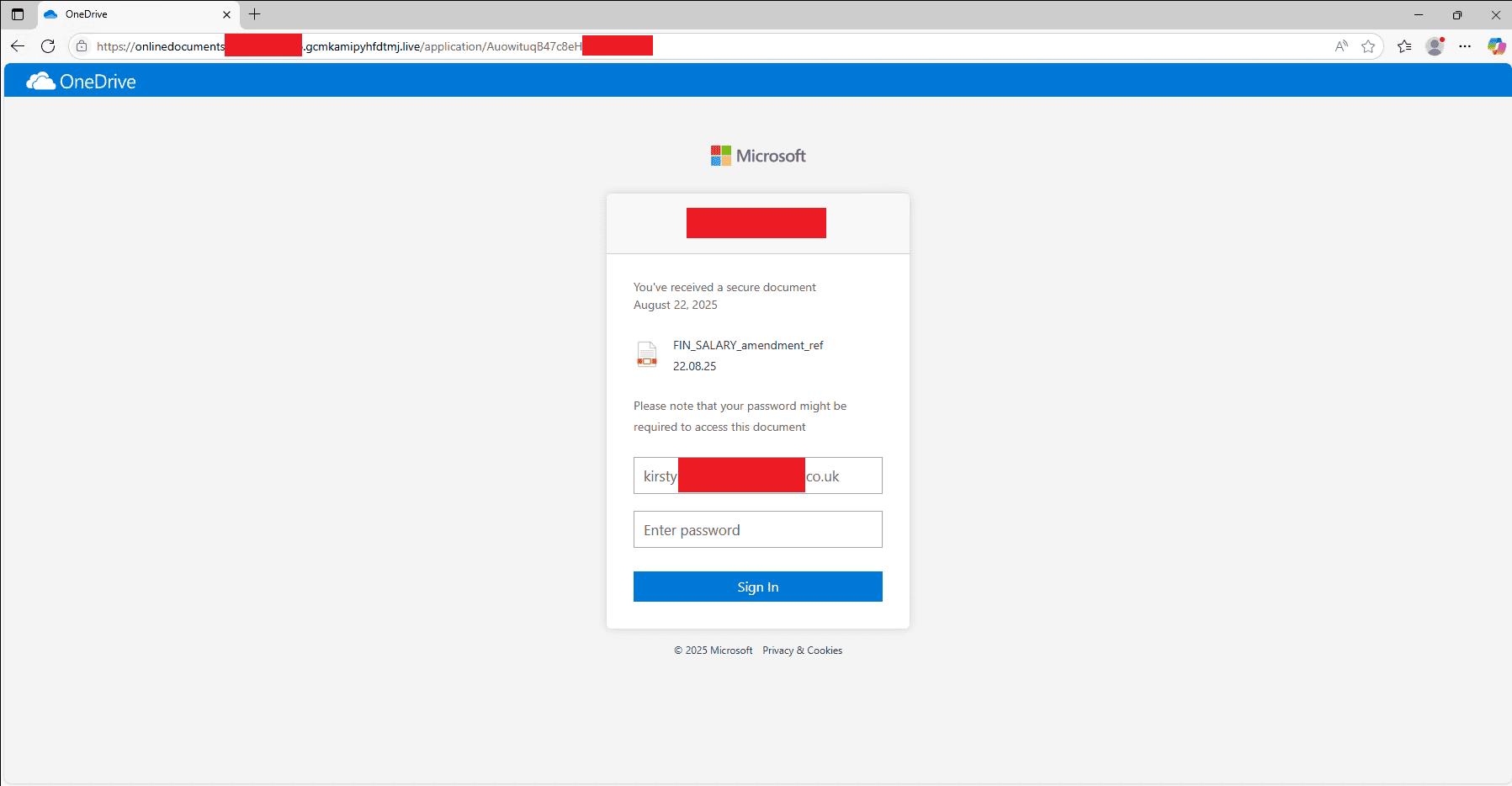
Researchers at Stripe OLT’s SOC have uncovered a large-scale, targeted phishing campaign aimed at senior executives and top managers across multiple industries. The attackers distribute emails disguised as internal correspondence from HR departments, inviting recipients to review alleged salary adjustments via a document hosted on OneDrive. Subjects such as “Salary amendment” or “FIN_SALARY” are commonly used. The embedded link redirects victims to a fraudulent Microsoft Office/OneDrive login page, crafted with striking authenticity and personalized details such as the employee’s name and company information—thereby enabling the theft of corporate credentials.
The campaign is meticulously orchestrated. Distribution relies on Amazon Simple Email Service (SES), while detection evasion is achieved through the use of more than eighty domains and subdomains. The attackers also employ a “warming” tactic: several days before the main attack, the target receives a harmless, neutral email, creating a false sense of trust. The phishing messages themselves contain hidden characters and external links to reputable resources, reducing the likelihood of detection by security filters. Each credential-harvesting URL is single-use and self-destructs once opened, eliminating the possibility of forensic re-examination.
The adversaries leverage multiple providers to maintain their infrastructure. Emails are routed through Amazon SES, DNS and nameserver services are often handled by Cloudflare, while the phishing pages have been hosted on Akamai Cloud (formerly Linode). Domain registration has predominantly been traced to Mat Bao Corporation, with additional registrars including WebNic.cc and Luxhost. Within the emails, evasion techniques are cleverly implemented: for example, in light mode, buttons appear simply as Open or Share, but in dark mode, hidden characters transform them into randomized strings such as twPOpenHuxv or gQShareojxYI, thereby breaking trigger words and thwarting pattern-based detection systems.
The campaign specifically targets employees with critical access to corporate data and resources. SOC experts warn that traditional user-awareness training alone is insufficient to mitigate such threats. Executives and their assistants are urged to exercise heightened caution when receiving unexpected emails—particularly those referencing salaries or HR matters—and to promptly report suspicious messages to security teams. For IT departments, proactive threat hunting for indicators of compromise and the blocking of malicious domains are vital. Microsoft Sentinel users are advised to deploy KQL queries to detect inbound emails with the subject line FIN_SALARY.
The investigation has already identified an extensive list of associated domains, including hr-fildoc[.]com, docutransit[.]com, seamlessshare[.]com, filershare[.]com, mysharedfiling[.]com, documentmagnet[.]com, signifile[.]com, and many others. All are tied to the current campaign and serve to bypass security systems while redirecting victims to counterfeit login portals. Analysts stress that the operation exemplifies the increasing sophistication of targeted phishing—marked by personalization, single-use URLs, and refined obfuscation techniques—making such campaigns particularly dangerous for organizations.