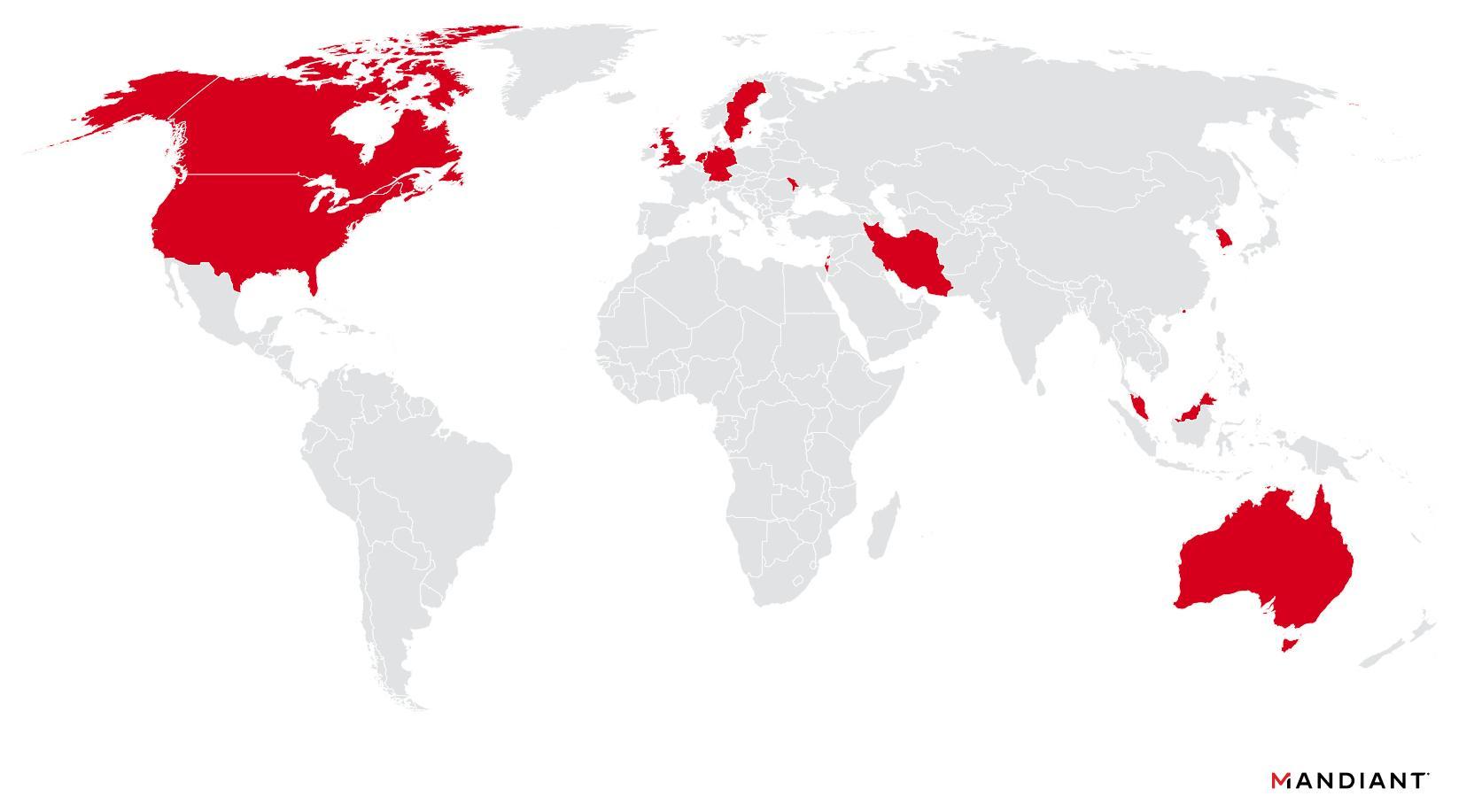
UNC5174 global targeting map
Mandiant specialists report that Chinese hackers, identified as UNC5174, are exploiting vulnerabilities in widely-used products to disseminate malicious software capable of installing additional backdoors on compromised Linux hosts.
The attacks orchestrated by UNC5174 have targeted a broad array of entities ranging from research and educational institutions in Southeast Asia and the United States to businesses in Hong Kong, philanthropic and non-governmental organizations, as well as governmental agencies in the U.S. and the U.K., spanning from October to November 2023 and again in February 2024.
The primary method for gaining initial access involved exploiting known vulnerabilities in systems such as:
- Atlassian Confluence (CVE-2023-22518, CVSS score: 9.8);
- ConnectWise ScreenConnect (CVE-2024-1709, CVSS score: 10.0);
- F5 BIG-IP (CVE-2023-46747, CVSS score: 9.8);
- Linux Kernel (CVE-2022-0185, CVSS score: 8.4);
- Zyxel (CVE-2022-3052, CVSS score: 5.4).
Following successful penetration, extensive reconnaissance and scanning activities were conducted to identify security vulnerabilities. UNC5174 also created administrator accounts to carry out malicious actions with elevated privileges.
The arsenal of the attackers included the SNOWLIGHT loader (based on C), designed to deliver the next stage’s payload—an obfuscated backdoor GOREVERSE (on Golang), which enables attackers to establish a reverse SSH tunnel and initiate interactive shell sessions for executing arbitrary code. Also discovered were tools for tunneling (GOHEAVY) and facilitating lateral movement within compromised networks (afrog, DirBuster, Metasploit, Sliver, and sqlmap).
An interesting tactic employed by the hackers was attempting to mitigate the vulnerability CVE-2023-46747 to prevent other malefactors from exploiting the same loophole. This move underscores the complexity and multi-layered nature of the campaign, where even hackers are compelled to take steps to ensure the “exclusivity” of access to compromised systems.
Mandiant suggests that UNC5174 may act as an Initial Access Broker (IAB), supported by China’s Ministry of State Security. This is corroborated by attempts to sell access to systems belonging to U.S. defense contractors, British government institutions, and Asian institutes.






