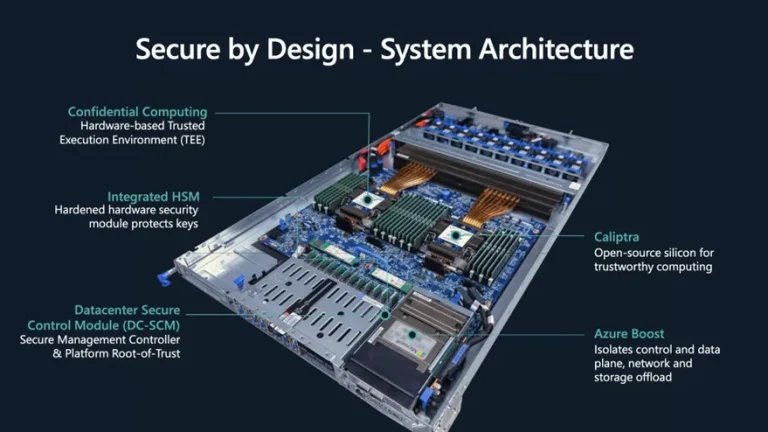
For many years, Microsoft has built its cloud security strategy around hardware, and after a string of...
confidential computing
Researchers at ETH Zurich have unveiled a novel attack against AMD’s SEV-SNP hardware isolation mechanism, enabling a...
At the Ignite 2020 conference held this week, Microsoft introduced the latest state of Azure confidential computing,...