Security experts at SafeBreach have disclosed the details of a vulnerability in the Windows Remote Procedure Call (RPC) protocol, patched by Microsoft in the July 2025 security update. Tracked as CVE-2025-49760 with a CVSS score of 3.5, the flaw allowed an attacker to perform spoofing attacks, impersonating a legitimate server through the Windows Storage mechanism. The discovery was presented by Ron Ben Yizhak at DEF CON 33.
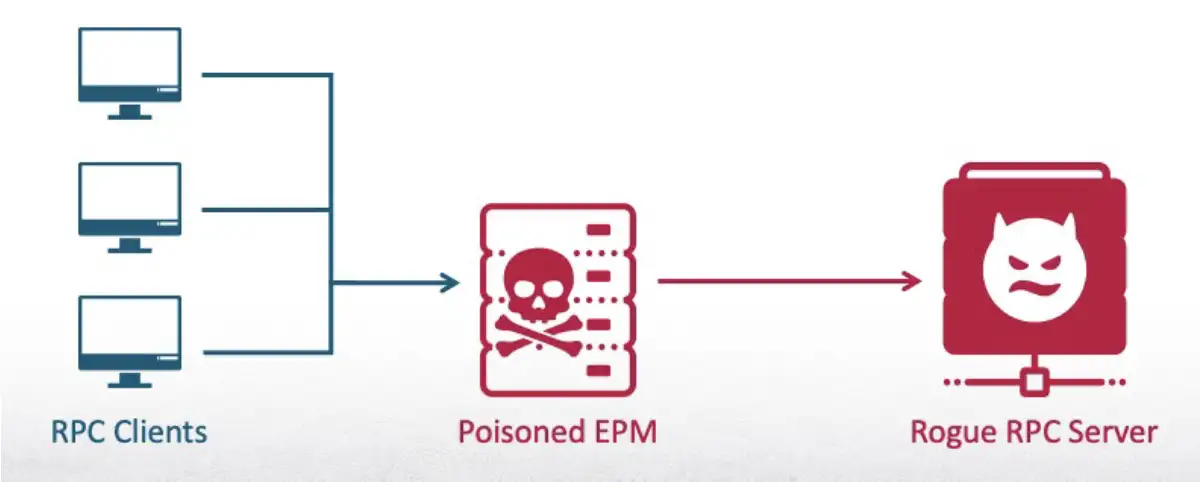
The RPC protocol relies on unique interface identifiers (UUIDs) and the Endpoint Mapper (EPM) service, which links client requests to the dynamic endpoints of registered servers. The flaw opened the door to an “EPM poisoning” attack, enabling a non-privileged user to register the interface of a built-in service and trick a protected process into authenticating to an arbitrary server. Similar to DNS spoofing, this technique replaces the UUID-to-endpoint mapping, redirecting the client to a malicious destination.
The issue was exacerbated by the fact that EPM does not validate the authenticity of the interface registrar. This allowed an attacker to preemptively register an interface belonging to a service with delayed or manual startup—before the legitimate process could claim it. As a result, the attacker could hijack connections without administrative privileges.
SafeBreach developed a tool, RPC-Racer, capable of detecting such insecure RPC services—such as Storage Service (StorSvc.dll)—and redirecting requests from a Protected Process Light (PPL) service, such as Delivery Optimization (DoSvc.dll), to a rogue SMB server. This would force the process to authenticate using the machine account, leaking the NTLM hash. The hash could then be leveraged in an ESC8 attack to escalate privileges via the Active Directory Certificate Services (AD CS). Using tools like Certipy, an attacker could obtain a Kerberos TGT and gain full access to all secrets stored on the domain controller.
The full attack chain involved creating a task triggered at user logon, registering the Storage Service interface, coercing Delivery Optimization to connect to the rogue server, supplying an SMB link to the malicious resource, and extracting the NTLM hash. The stolen NTLM credentials could then be exchanged for a certificate, granting domain-level privileges.
Beyond direct privilege escalation, EPM poisoning could also facilitate Man-in-the-Middle (MitM) attacks by proxying requests to the original service, or denial-of-service scenarios by registering numerous interfaces and blocking legitimate requests. SafeBreach warns that other system clients may be equally vulnerable to such interception.
To detect such attacks, researchers recommend monitoring RpcEpRegister calls and leveraging Event Tracing for Windows (ETW) to log events generated by applications and drivers. They suggest that, much like SSL pinning validates a specific key, EPM should authenticate the identity of the RPC server—otherwise, clients risk placing blind trust in unverified sources.