Researchers at Eclypsium have uncovered critical vulnerabilities in the Lenovo 510 FHD and Lenovo Performance FHD webcams that allow them to be transformed into BadUSB-style attack devices. The issue, dubbed BadCam, was presented at DEF CON 33 and is believed to be the first documented case in which a Linux-based device, already connected to a computer, can be remotely reprogrammed and repurposed as a malicious USB peripheral.
BadUSB attacks have been known since 2014, when Karsten Nohl and Jakob Lell demonstrated that USB device firmware could be reflashed to surreptitiously execute commands and run malicious code. Unlike conventional malware residing in the file system, such attacks operate at the firmware level, rendering them virtually invisible to antivirus software. Compromised devices can emulate keyboards, intercept input, install backdoors, reroute network traffic, and exfiltrate data.
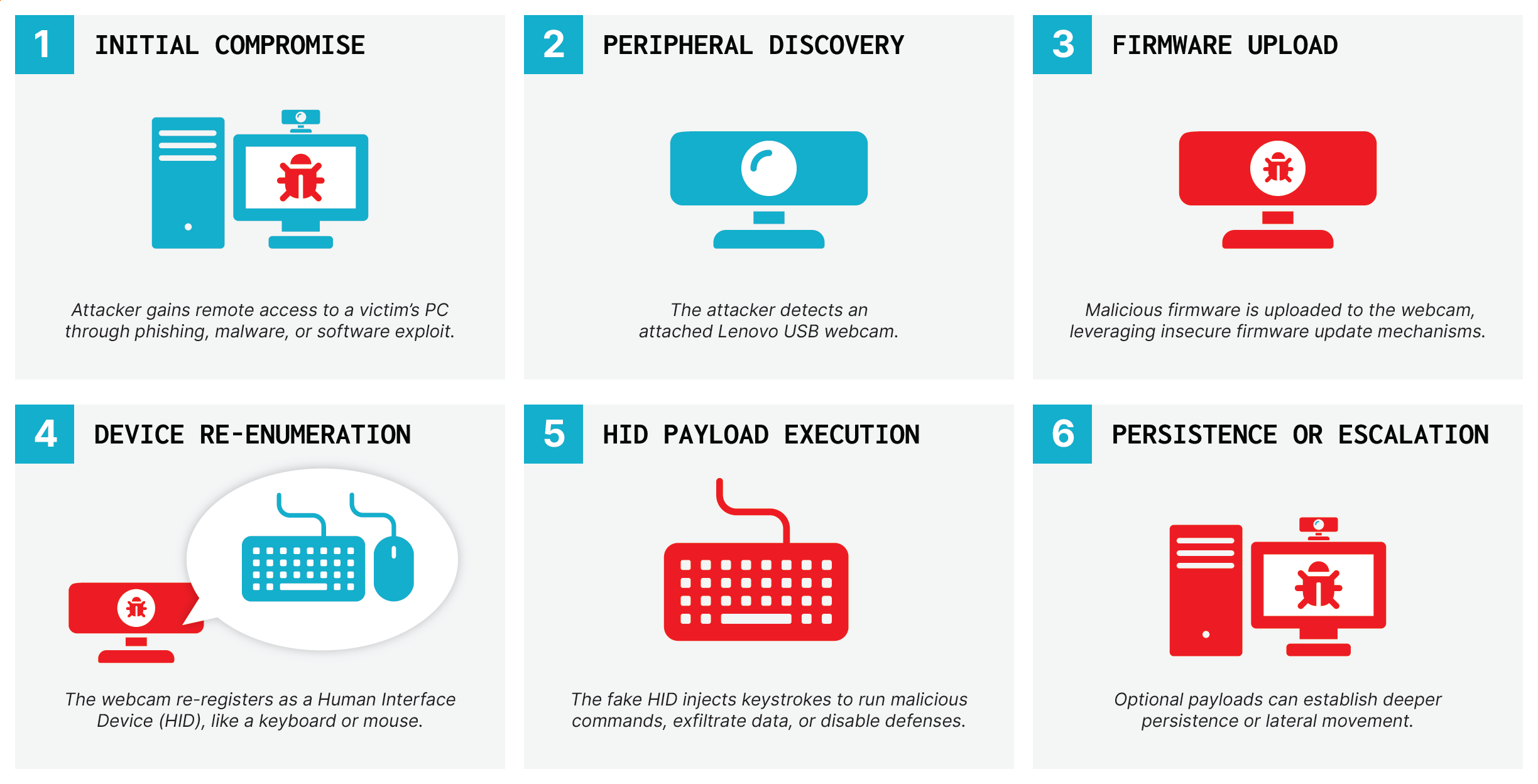
According to the scenario described by the researchers, an attacker could send a victim a compromised webcam or physically connect one to a target machine, then remotely seize control. Once compromised, the device can function as an HID emulator or an additional USB device—issuing commands, delivering payloads, and establishing persistence—while still operating as a fully functional camera. More alarmingly, a camera reprogrammed in this way could reinfect a computer even after the operating system has been reinstalled.
The root cause lies in the absence of firmware authenticity checks and the presence of USB Gadget support in Linux, which together allow complete compromise of the device’s software stack. Following the disclosure in April 2025, Lenovo released firmware update version 4.8.0 and, in collaboration with SigmaStar, provided a tool to remediate the flaw.
Experts warn that this attack highlights a serious gap in the trust model: both corporate and consumer systems often automatically trust peripherals capable of executing code and accepting remote instructions. Vulnerable devices may pose a threat not only to the system they are currently connected to, but to any other machine they are subsequently plugged into.