kubeeye
KubeEye is an audit tool for Kubernetes to discover Kubernetes resources (by OPA ), cluster components, cluster nodes (by Node-Problem-Detector), and other configurations that are meeting with best practices and giving suggestions for modification.
KubeEye supports custom audit rules and plugins installation. Through KubeEye Operator, you can view audit results and modify suggestions on the website.
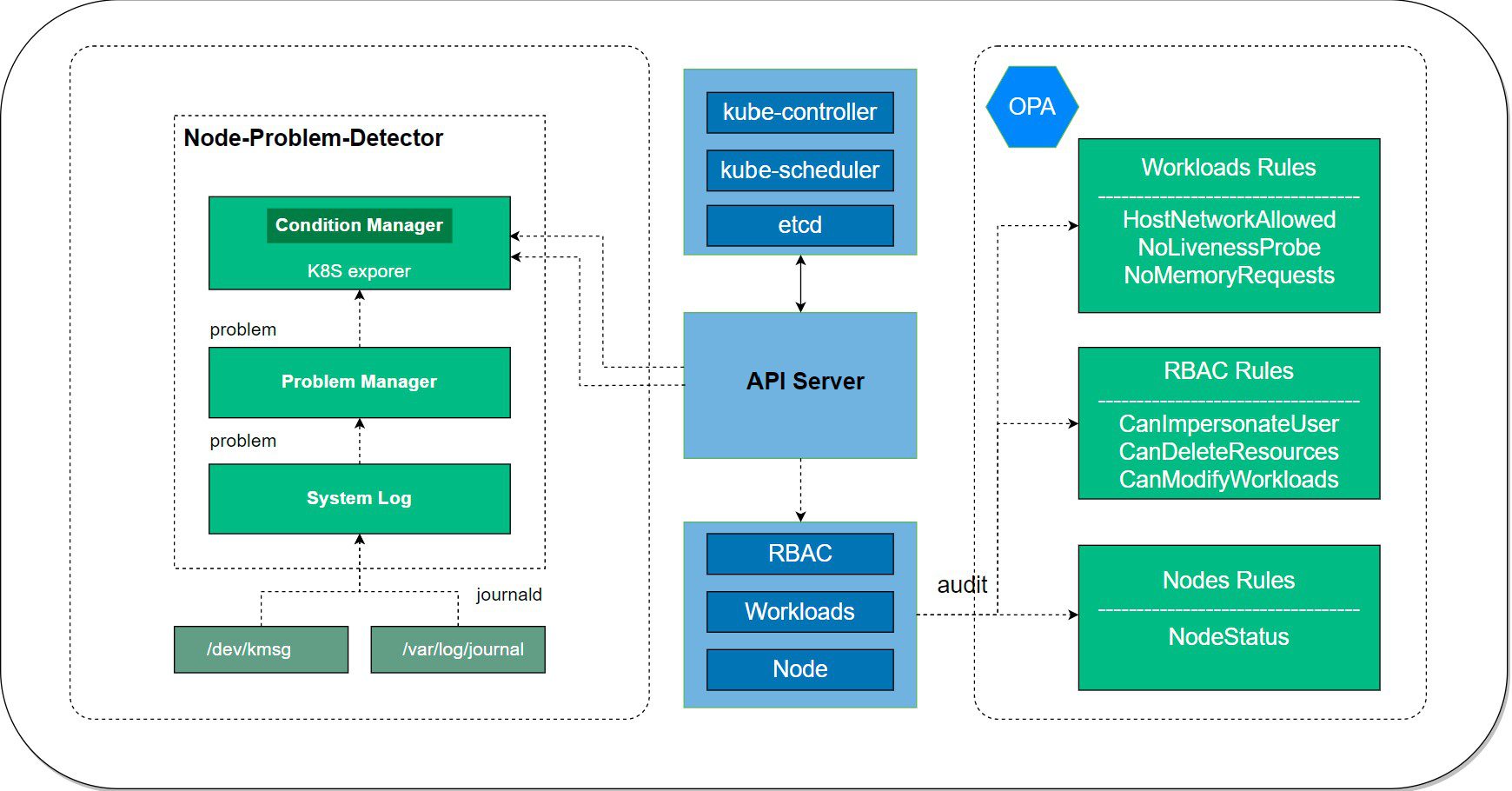
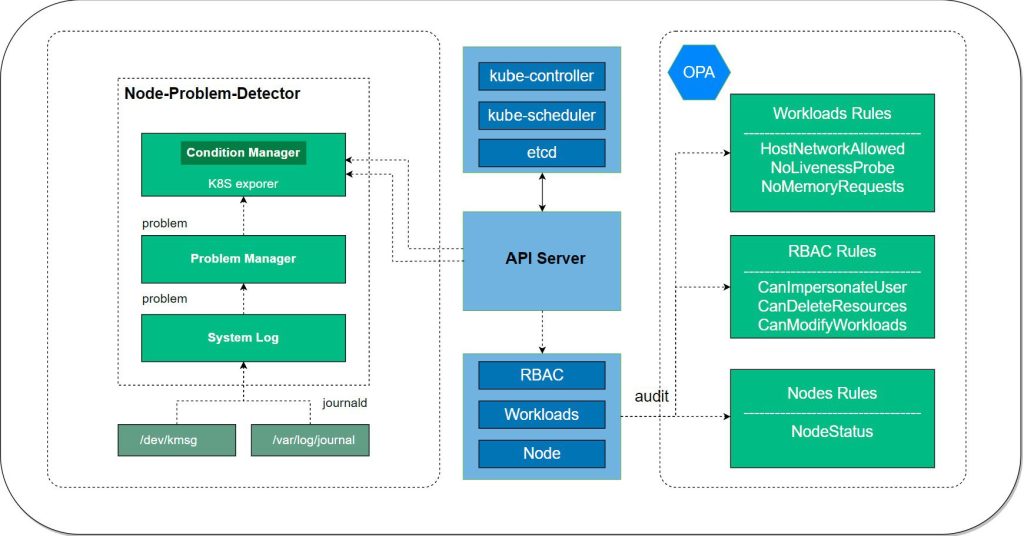
Architecture
KubeEye gets cluster resource details by the Kubernetes API, audits the resource configurations by audit rules and plugins, and generates audit results. See Architecture for details.
What KubeEye can do
- KubeEye audits cluster resources with Kubernetes best practices, to make cluster stable.
- KubeEye can find problems of your cluster control plane, including kube-apiserver/kube-controller-manager/etcd, etc.
- KubeEye helps you detect all kinds of node problems, including memory/cpu/disk pressure, unexpected kernel error logs, etc.
Checklist
| YES/NO | CHECK ITEM | Description | Level |
|---|---|---|---|
| ✅ | PrivilegeEscalationAllowed | Privilege escalation is allowed | danger |
| ✅ | CanImpersonateUser | The role/clusterrole can impersonate other user | warning |
| ✅ | CanModifyResources | The role/clusterrole can delete kubernetes resources | warning |
| ✅ | CanModifyWorkloads | The role/clusterrole can modify kubernetes workloads | warning |
| ✅ | NoCPULimits | The resource does not set limits of CPU in containers.resources | danger |
| ✅ | NoCPURequests | The resource does not set requests of CPU in containers.resources | danger |
| ✅ | HighRiskCapabilities | Have high-Risk options in capabilities such as ALL/SYS_ADMIN/NET_ADMIN | danger |
| ✅ | HostIPCAllowed | HostIPC Set to true | danger |
| ✅ | HostNetworkAllowed | HostNetwork Set to true | danger |
| ✅ | HostPIDAllowed | HostPID Set to true | danger |
| ✅ | HostPortAllowed | HostPort Set to true | danger |
| ✅ | ImagePullPolicyNotAlways | Image pull policy not always | warning |
| ✅ | ImageTagIsLatest | The image tag is latest | warning |
| ✅ | ImageTagMiss | The image tag do not declare | danger |
| ✅ | InsecureCapabilities | Have insecure options in capabilities such as KILL/SYS_CHROOT/CHOWN | danger |
| ✅ | NoLivenessProbe | The resource does not set livenessProbe | warning |
| ✅ | NoMemoryLimits | The resource does not set limits of memory in containers.resources | danger |
| ✅ | NoMemoryRequests | The resource does not set requests of memory in containers.resources | danger |
| ✅ | NoPriorityClassName | The resource does not set priorityClassName | ignore |
| ✅ | PrivilegedAllowed | Running a pod in a privileged mode means that the pod can access the host’s resources and kernel capabilities | danger |
| ✅ | NoReadinessProbe | The resource does not set readinessProbe | warning |
| ✅ | NotReadOnlyRootFilesystem | The resource does not set readOnlyRootFilesystem to true | warning |
| ✅ | NotRunAsNonRoot | The resource does not set runAsNonRoot to true, maybe executed run as a root account | warning |
| ✅ | CertificateExpiredPeriod | Certificate expiration date less than 30 days | danger |
| ✅ | EventAudit | Event audit | warning |
| ✅ | NodeStatus | node status audit | warning |
| ✅ | DockerStatus | docker status audit | warning |
| ✅ | KubeletStatus | kubelet status audit | warning |
Install & Use
Copyright (C) 2022 kubesphere