The Iran-Nexus Spear phishing Campaign attack path
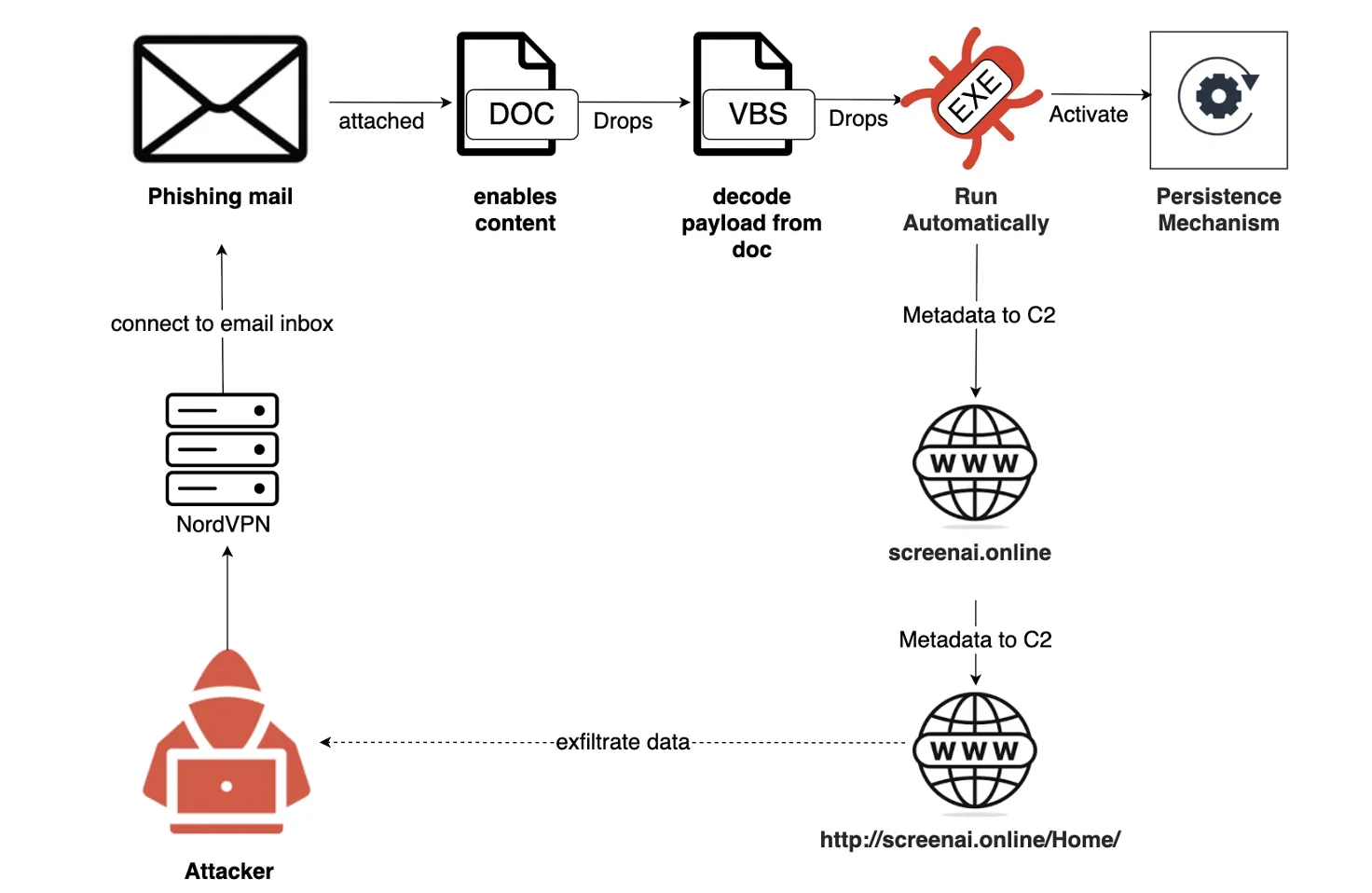
In August 2025, specialists from Dream Threat Intelligence documented a large-scale phishing campaign attributed to actors linked to Iran. The operation, believed to be orchestrated by the group Homeland Justice under the direction of Iran’s Ministry of Intelligence and Security (MOIS), was disguised as official diplomatic correspondence from Oman’s Ministry of Foreign Affairs. The attackers leveraged a compromised mailbox of the Omani Embassy in Paris, distributing malicious emails to government bodies and international organizations worldwide.
According to analysts, the embedded macro extracted an encrypted numeric sequence from a hidden form field, decoding it by converting three-digit segments into ASCII characters. The resulting executable file was stored under the guise of a log file—ManagerProc.log—within C:\Users\Public\Documents and executed silently without any visible user interface. To enhance stealth, the malware employed classic evasion tactics: launching with the vbHide parameter, introducing execution delays, suppressing error messages, and masquerading code as a harmless log. It then copied itself to C:\ProgramData\sysProcUpdate.exe for persistence, subsequently modifying DNS and TCP/IP settings in the system registry to impede detection and ensure long-term presence.
Once deployed, sysProcUpdate collected information such as username, computer name, and privilege level, generating a JSON payload transmitted via HTTPS to a remote C2 server at https://screenai.online/Home/. In sandbox tests, the connection failed, suggesting the server was either blocked or temporarily offline. Still, repeated TLS connection attempts to the domain over port 443 were recorded among the network indicators of compromise.
The campaign exhibited both scale and sophistication. At least 104 compromised email addresses were used to obscure its origin, while outbound traffic was routed through VPN servers. The attack spanned multiple regions—including the Middle East, Europe, Asia, Africa, and the Americas—tailored to the context of each target. Some phishing lures referenced “The Future of the Region after the Iran–Israel Conflict and the Role of Arab States in the Middle East,” underscoring the use of geopolitical tension as bait.
The infrastructure blended legitimate government domains (e.g., @fm.gov.om), VPN nodes, and malicious hosting at screenai.online. Attachments mimicked official MFA documents, urging recipients to “unlock content” by enabling macros. In several cases, recipients saw Ukrainian-language Proofpoint warning banners, suggesting intrusions into organizations using localized security tools.
Dream’s assessment concludes that the operation bore the hallmarks of an intelligence-gathering campaign, likely intended as a precursor to data exfiltration or lateral movement. The attackers combined highly customized phishing lures, social engineering, and technical evasion, demonstrating both professional tradecraft and an intimate understanding of diplomatic ecosystems. The most probable objectives included reconnaissance, foothold establishment, and sustained infiltration of critical institutions.
Experts recommend the immediate blocking of all identified indicators of compromise, monitoring outbound POST requests to URLs containing /Home/, auditing registry keys for unauthorized network modifications, and disabling Microsoft Office macros by default. Additionally, organizations should review VPN logs for anomalous connections from atypical regions and implement network segmentation to restrict outbound traffic.
Taken together, the evidence points to a sophisticated, multi-stage espionage operation, carefully masked and directed primarily at diplomatic entities in Europe and the Middle East, with strong potential to escalate into deeper phases of intrusion.





