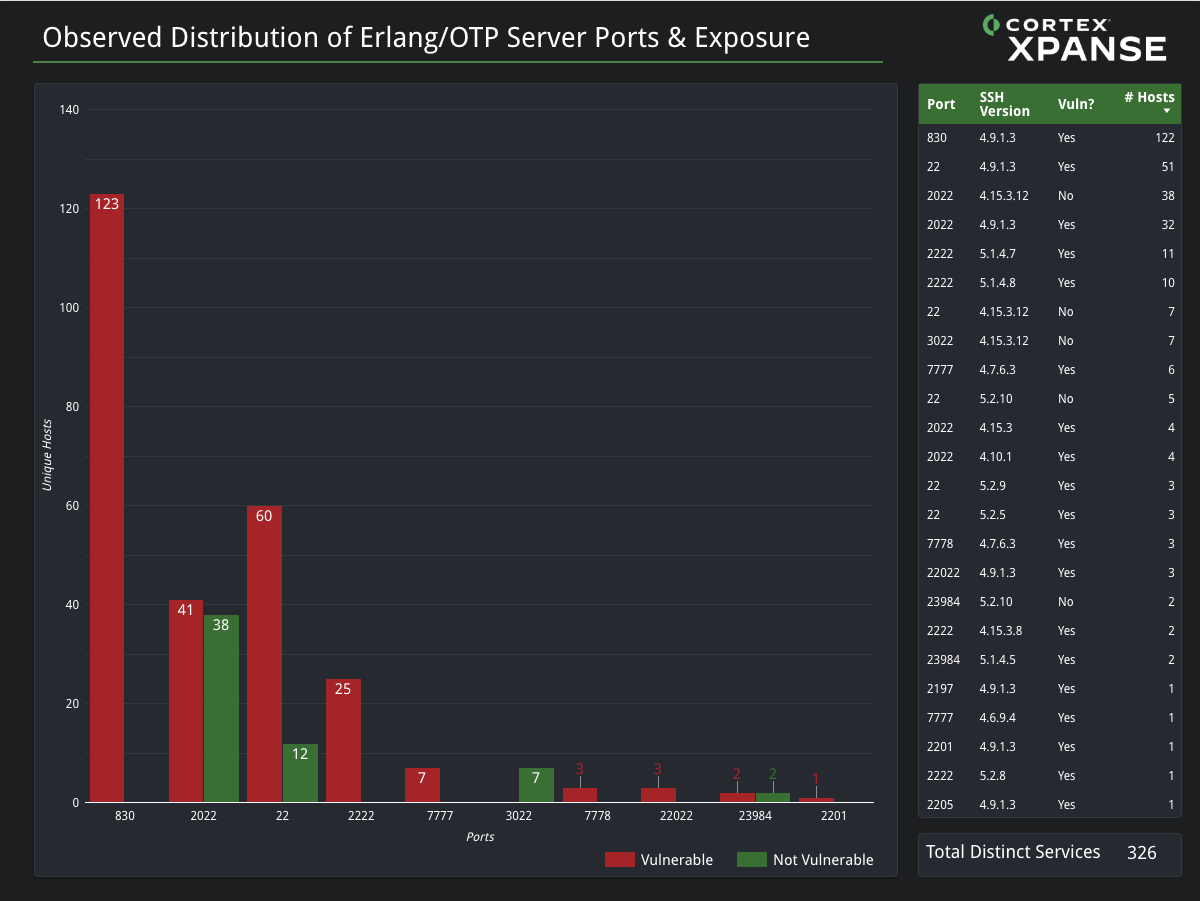
Researchers have determined that a critical flaw in the SSH stack implementation of Erlang/Open Telecom Platform had been actively exploited as early as May 2025, with roughly 70% of detections targeting firewalls safeguarding industrial network segments. The campaign unfolded even after fixes had been released: patches were issued in April in OTP versions 27.3.3, 26.2.5.11, and 25.3.2.20.
The vulnerability, assigned CVE-2025-32433 and rated at the maximum CVSS score of 10.0, stems from missing authentication in the native SSH implementation. With network access to the Erlang/OTP service, an attacker could execute arbitrary code without any credentials. Since the embedded SSH service handles not only encrypted sessions but also file transfers and remote command execution, such a defect poses a direct threat to every exposed instance.
In June 2025, CISA added CVE-2025-32433 to its Known Exploited Vulnerabilities (KEV) catalog, confirming verified exploitation in the wild. Analysts from Palo Alto Networks Unit 42 — Adam Robby, Yihan An, Malav Vyas, Cecilia Hu, Matthew Tennis, and Zhanghao Chen — emphasize that this failure within the subsystem enables passwordless compromise, rendering vulnerable nodes exceptionally easy targets.
Telemetry shows that over 85% of attempts were directed at the healthcare, agriculture, media, and high-tech industries. The geographic scope is broad, including the United States, Canada, Brazil, India, Australia, and other regions. Observed patterns involved short bursts of high-intensity activity, focusing primarily on OT networks, with adversaries probing both conventional IT ports and specialized industrial services.
When successful, the intrusions leveraged reverse shells to gain remote access and establish persistence within the victim’s infrastructure, followed by reconnaissance, data exfiltration, and lateral movement. The identity of the group behind this wave remains undetermined.
Open services on ports typical for industrial systems indicate that OT networks worldwide still present a vast attack surface. While the exact nature of the assaults varied, the overarching picture was consistent: brief surges of activity, a pronounced focus on OT, and simultaneous exploitation attempts via both IT and industrial gateways — all pointing to a calculated adversary strategy aimed at seizing vulnerable points before administrators could deploy patches.