On August 26, China hosted the 2025 China Operating System Industry Conference, jointly organized by the China...
Technology
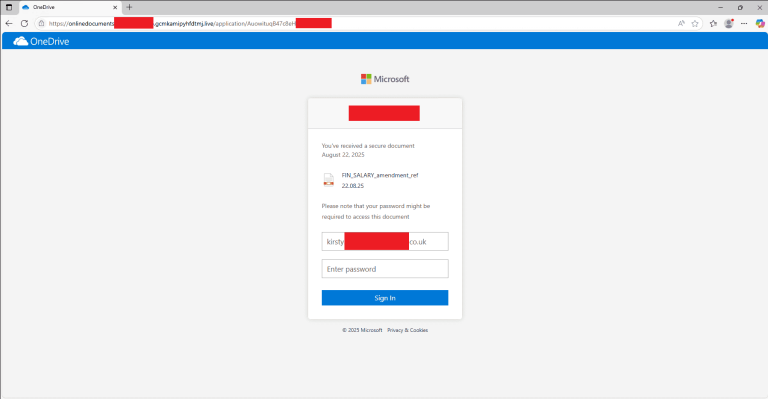
Entrepreneur Dan Shapiro encountered an unexpected obstacle: a popular AI chatbot refused to transcribe business documents, citing...
Amnesty International has released a new report titled Breaking up with Big Tech, calling on governments to...
Electronic Arts has taken a controversial step in the open beta test of Battlefield 6 for PC:...
Earlier this month, a Florida court found Tesla partially liable in a case concerning the death of...
A recently published study has revealed an unexpected trend: seasoned developers with a decade of experience are...
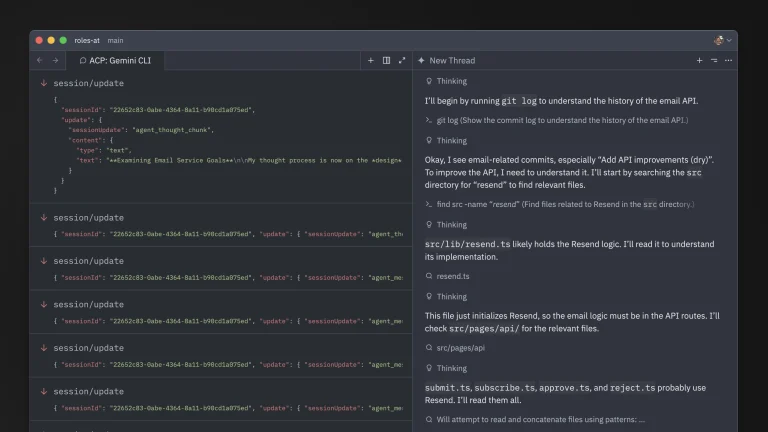
Google and Zed Industries have announced the launch of the Agent Client Protocol (ACP) — a new...
A new version of the widely used multimedia framework FFmpeg — 8.0 “Huffman” — has been released,...
On August 27, 2025, at the Open Source Summit Europe, the LF Networking (LFN) community, part of...
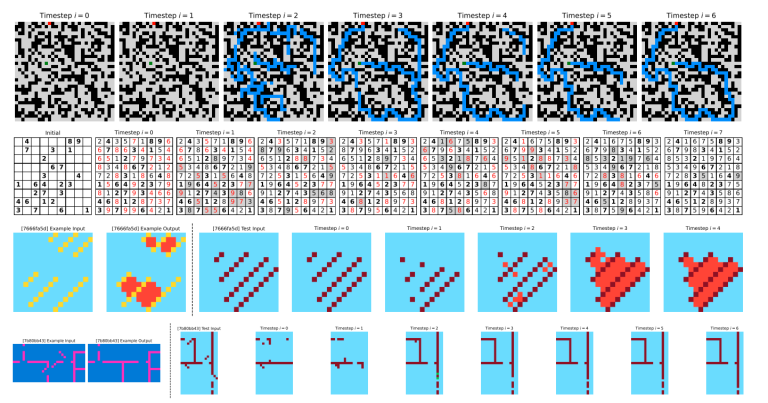
Scientists at the Singapore-based company Sapient have unveiled a novel approach to artificial intelligence that operates in...
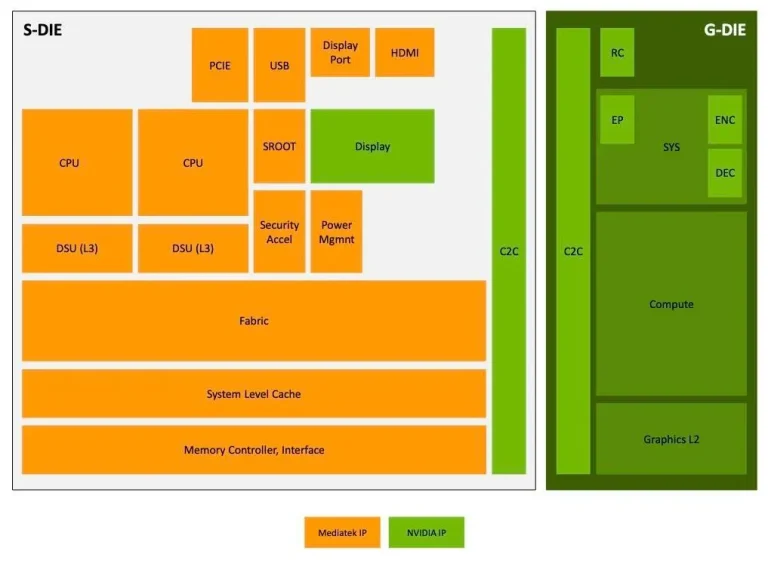
In 2023, Nvidia unveiled a groundbreaking superchip architecture that unites CPU and GPU through the high-speed NVLink...
GitHub has announced the launch of the public preview of the Grok Code Fast 1 model in...
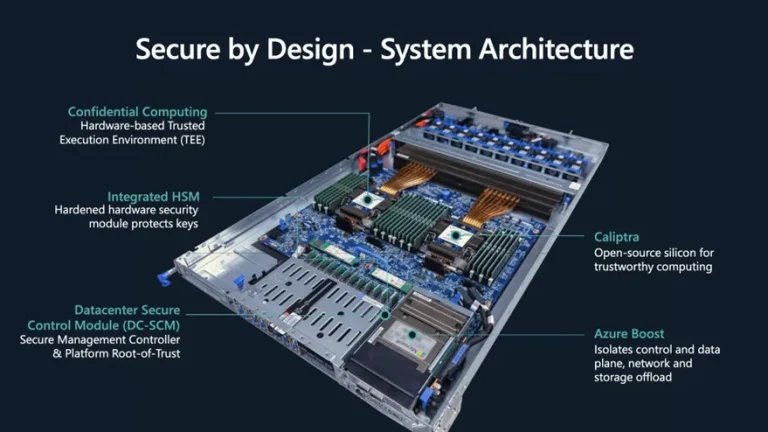
For many years, Microsoft has built its cloud security strategy around hardware, and after a string of...
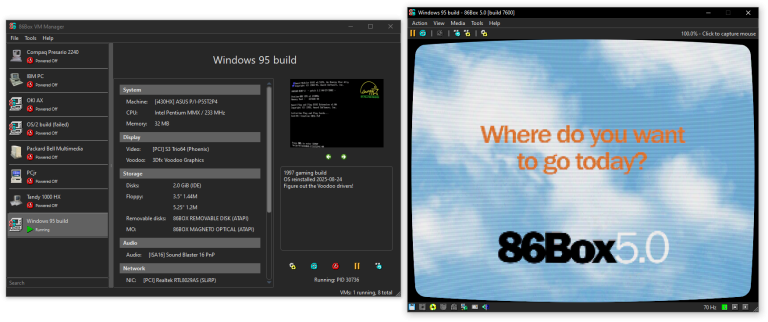
The 86Box project has released version 5.0 of its x86-based computer emulator, enabling users to run legacy...
The U.S. Federal Trade Commission (FTC) has issued a stern warning to America’s largest technology companies, declaring...
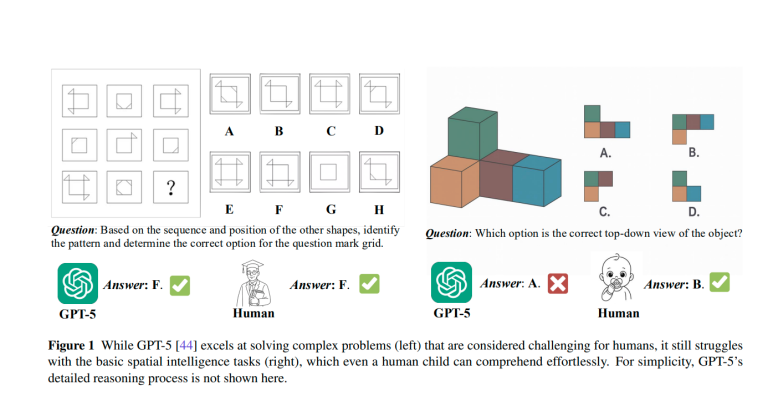
Researchers from SenseTime Research and the S-Lab at Nanyang Technological University have presented a comprehensive technical report...