Media Info Exploit
Bluetooth-enabled devices produced by a dozen renowned manufacturers have been found vulnerable to attacks capable of transforming wireless headsets or speakers into espionage tools. This alarming revelation was presented by experts from ERNW during the TROOPERS security conference held in Germany. According to their findings, compromised Airoha chips are embedded in 29 device models from prominent brands including Beyerdynamic, Bose, Sony, Marshall, Jabra, JBL, Jlab, EarisMax, MoerLabs, and Teufel.
The affected list encompasses not only common headphones and headsets but also portable speakers, wireless microphones, and other audio devices. The vulnerabilities reside in Airoha’s system-on-chip (SoC) architectures, which are widely integrated into popular wireless accessories, including true wireless stereo (TWS) earbuds.
The researchers identified three critical vulnerabilities, each assigned a distinct CVE identifier:
- CVE-2025-20700 (CVSS score: 6.7) — absence of authentication checks for GATT services;
- CVE-2025-20701 (CVSS score: 6.7) — lack of authentication during Bluetooth BR/EDR pairing;
- CVE-2025-20702 (CVSS score: 7.5) — severe flaws in the vendor’s proprietary protocol.
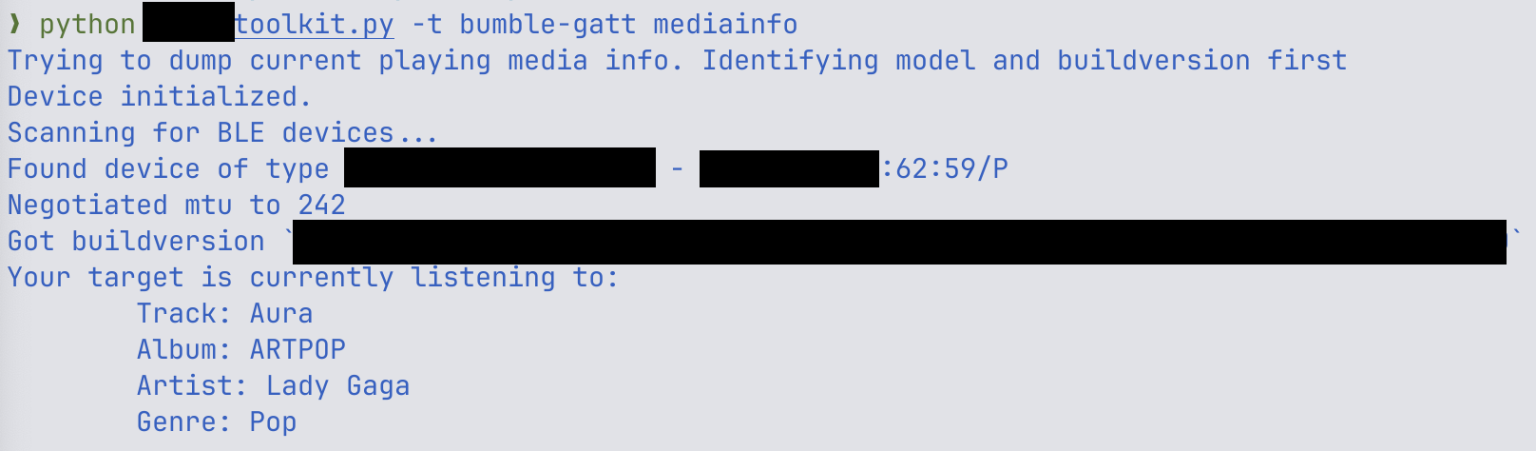
Although successful exploitation requires the attacker’s physical proximity and advanced technical proficiency, the potential threat scenarios are deeply concerning. ERNW researchers developed a functional proof-of-concept that allows the extraction of live audio streams—such as currently playing music—from a user’s headphones.
A graver concern arises from the ability to hijack the connection between a smartphone and a headset. Via the Bluetooth Hands-Free Profile (HFP), an attacker can issue commands to the smartphone. According to the researchers, all major mobile platforms permit headsets to at least initiate or accept calls.
By exploiting the disclosed vulnerabilities, the researchers demonstrated their ability to extract Bluetooth session keys from a headset’s memory. This enables the substitution of the legitimate device with a malicious clone, allowing interception of the connection—and, in some cases, access to call logs or contact lists stored on the phone.
In particular configurations, an attacker could initiate arbitrary calls and covertly listen to conversations or ambient audio, effectively transforming the phone into a surveillance instrument.
Of particular concern is the potential for malicious firmware updates. This opens the door to implanting harmful code or, in a worst-case scenario, crafting a self-propagating exploit capable of spreading via Bluetooth to other nearby devices.
Despite the severity of the threat, experts emphasize that such attacks are highly unlikely to occur on a mass scale. Their execution demands not only an intricate understanding of Bluetooth protocols and Airoha’s architecture but also physical proximity to the target. Therefore, likely victims would be high-value individuals such as journalists, diplomats, business executives, or activists.
Airoha has already released an updated SDK incorporating the necessary security patches. Device manufacturers have begun developing corresponding firmware updates. However, the German publication Heise reports that, as of late June, most vulnerable models have yet to receive these critical patches—leaving users currently unable to safeguard their devices.
Until firmware updates are both issued by manufacturers and installed by end users, owners of popular headphones and speakers remain at risk. Comprehensive protection will only materialize once these updates are widely deployed.