Amid the growing popularity of Android smartphones in developing regions and the increasing accessibility of third-party app stores, cybercriminals have launched a large-scale campaign that combines two highly dangerous tactics—credential theft and click fraud—for a covert yet extremely lucrative malicious operation.
By crafting specially designed APK files, attackers disguise malware as legitimate applications and distribute them outside official channels, including through phishing messages and fake promotional pages mimicking well-known brands.
The apps are presented as popular services, reward-based programs, utilities, gambling platforms, or tools purportedly from reputable companies, thereby gaining user trust. Once installed, these applications gain access to a wide range of system resources—ranging from geolocation and contact lists to call logs and unique device identifiers. In addition to harvesting sensitive information, they deploy concealed mechanisms to hijack traffic and interact automatically with advertising platforms, generating fake clicks, impressions, and installs.
Analysis has uncovered numerous APKs with varying levels of sophistication, all sharing a common architecture and linked to a singular malicious cluster. Some variants are exclusively focused on fabricating ad interactions, performing little else. Others are engineered to steal credentials by mimicking banking or social media interfaces.
There are also variants that discreetly harvest user data under the guise of games or utilities. Some promise rewards for simple actions but abuse permissions and surreptitiously transmit information to remote servers. A separate category includes gambling-themed apps that exploit legal loopholes while collecting both financial and personal data.
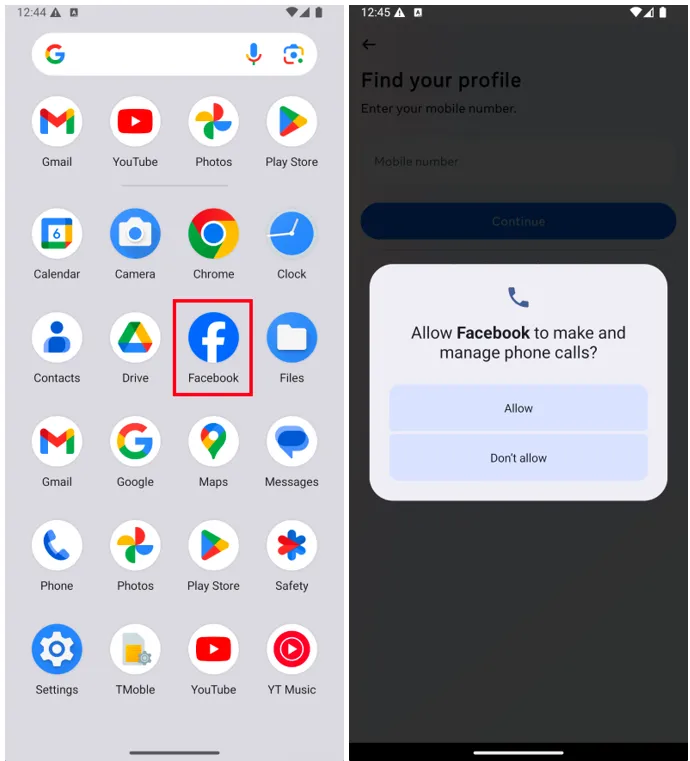
One of the most notable cases involves a counterfeit Facebook client, disseminated via fake domains that closely resemble legitimate URLs. It requests an extensive set of permissions—including precise location access—disguised as system components.
Upon installation, the app downloads encrypted configurations using AES-ECB and alters its behavior based on the execution environment. If launched on virtualized systems or emulators such as Genymotion, it may delay or entirely suppress its malicious payload. In real-world environments, it connects to command-and-control servers masquerading as telemetry services, transmitting data on the platform, locale, user metadata, and other parameters.
Technical analysis revealed the use of ApkSignatureKillerEx—a tool designed to bypass Android’s signature verification and inject secondary components, such as the stealthy “origin.apk” that runs in the background. The malicious infrastructure is built on segmented subdomains arranged in a hierarchical structure with adaptive behavior. Some samples target specific countries or languages, pointing to a highly focused strategy. Code fragments in Simplified Chinese, servers hosted on Alibaba Cloud, and the malware’s architecture all reflect a “Malware-as-a-Service” (MaaS) model—enabling scalable attacks and future exploitation of stolen data.
According to a report by Trustwave, the campaign merges two potent incentives: financial gain through ad fraud and the strategic collection of credentials for potential subsequent attacks. This highlights the hybrid nature of modern threats—surface-level activity may serve as a smokescreen for far more insidious and enduring exploitation.
To mitigate these risks, experts strongly advise downloading apps solely from trusted sources, remaining cautious of invitations to install APKs via messages or promotions, and carefully reviewing requested permissions.
At the organizational level, it is imperative to strengthen oversight of the mobile app supply chain, implement behavioral monitoring of installed software, and prioritize user education—particularly in regions more susceptible to such deceptive campaigns.






