Admin Panel Finder
A Burp Suite extension that enumerates infrastructure and application Admin Interfaces.
OWASP References:
- Classification: Web Application Security Testing > 02-Configuration and Deployment Management Testing
- OTG v4: OWASP OTG-CONFIG-005
- WSTG: WSTG-CONF-05
Why should I use this extension?
- Multi-thread
- Different and configurable levels of test.
- Includable status codes
- Excludable status codes
- More than 1000 built-in payloads.
- You can load your dictionary.
- Editable root directory
- Automatic detection of used technologies to generate custom payloads.
- Passive listening to find login pages.
Installation
git clone https://github.com/moeinfatehi/Admin-Panel_Finder.git
The quickest way is to load the jar file (adminPanelFinder.jar) in the extender tab of the Burpsuite.
Extender -> Extensions -> Add
A new tab will be added to the burp suite.
Quick Start

- Select a request of a target host from any tab of the burp suite (it must have a response with any status code)
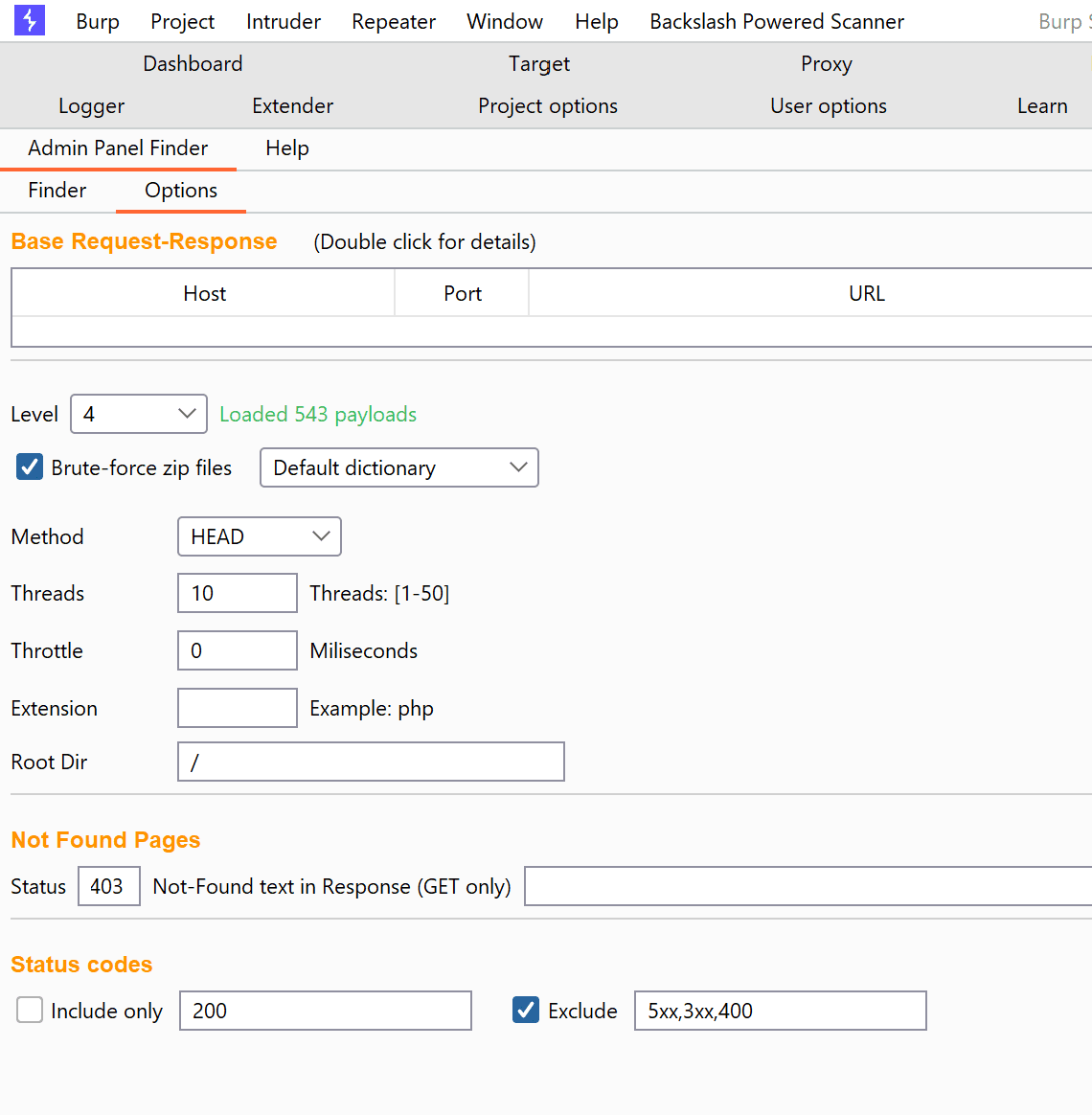
- In the “Admin Panel Finder -> options” tab, apply your configurations.
- Go to the “Admin Panel Finder -> Finder -> Finder” tab and click on the “start” button.
Some of the options
These options can be used to customize the detection:
- Level: Level of tests to perform (1-5, default 3)
- Thread: num of threads (1-50, default 10)
- Built-in dictionary: there is a built-in dictionary containing the most used directory and file names to be used for static payload generation.
- Loadable dictionary: you can use your dictionary file for static payload generation.
- HTTP method: HTTP method to be used in requests (HEAD, GET)(default: Head)
- Extension: The extension used in application pages. [Example: php, asp, aspx, jsp, …]
- Root Dir: The path to the root directory of the web application. (Default: /)
- Includable status codes
- Excludable status codes
Copyright (C) 2022 moeinfatehi