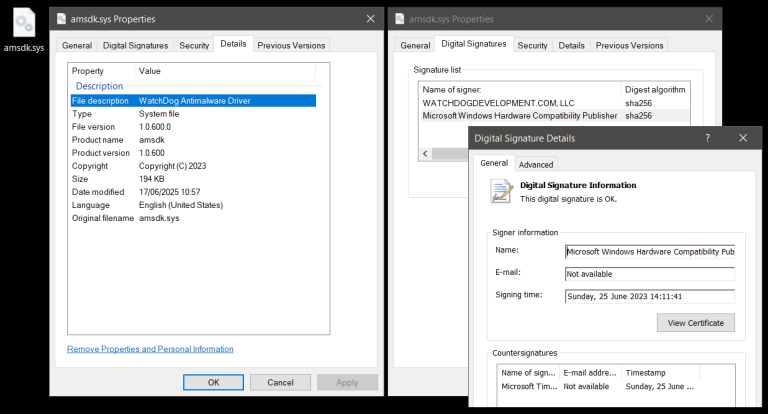
A group of hackers orchestrated a meticulously planned campaign targeting Gmail users, successfully bypassing two-factor authentication and...
phishing
At first glance, WormGPT appears to be a formidable tool in the arsenal of cybercriminals—powerful, unregulated, capable...
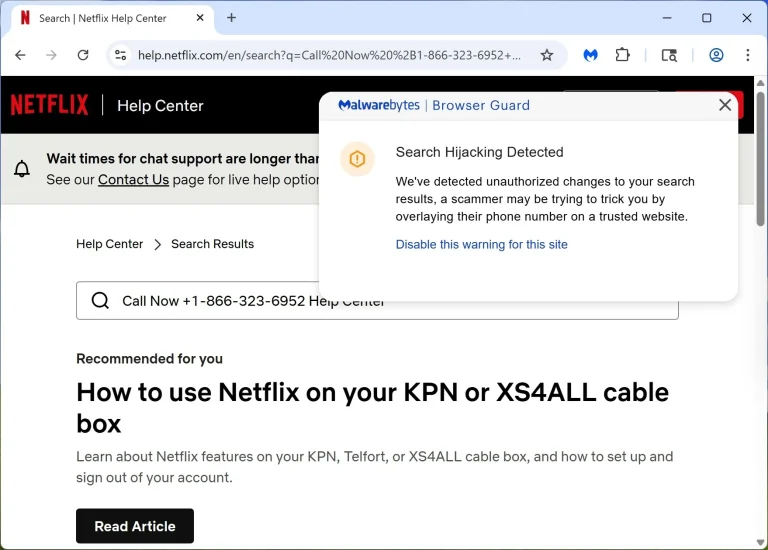
Fraudsters have developed a method to intercept search queries from users seeking 24/7 customer support from companies...
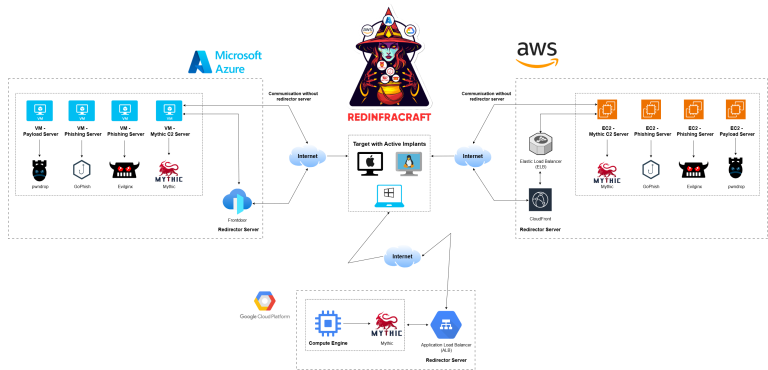
Welcome to the RedInfraCraft (V2) Tool – your gateway to automating the deployment of robust red team infrastructures! RedInfraCraft...
User credentials – logins and passwords for accessing various services – have become some of the most...