The top spot in HackerOne’s global ranking is no longer held by a human, but by a...
Offensive Security
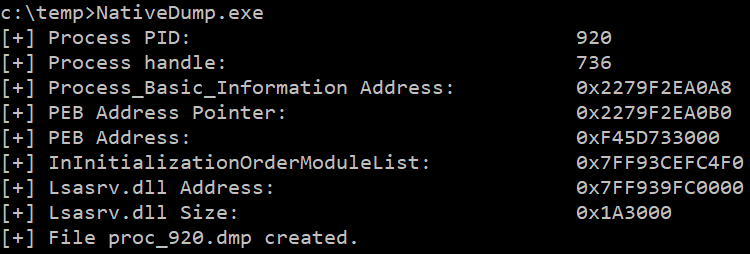
NativeDump allows to dump the lsass process using only NTAPIs generating a Minidump file with only the...
Bolthole A proof-of-concept ClickOnce payload for Red Teams to establish initial access in authorized penetration tests. Overview...
The emergence of a new tool known as RingReaper has sparked concern among cybersecurity experts and penetration...
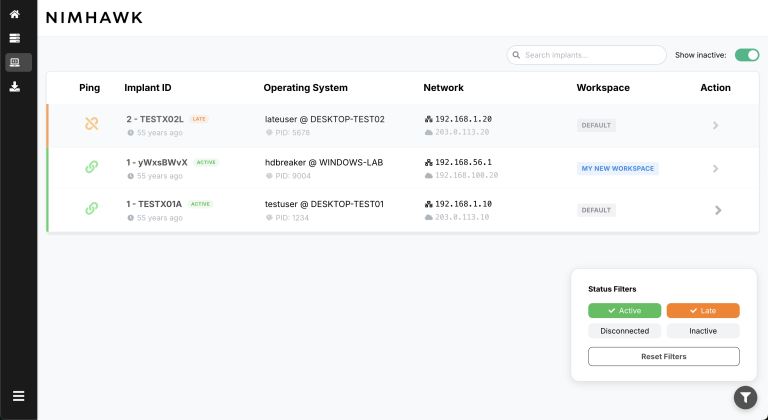
Nimhawk is an advanced command and control (C2) framework that builds upon the exceptional foundation laid by Cas...
ZigStrike is a robust shellcode loader developed in Zig, offering a variety of injection techniques and anti-sandbox...
Hollowise is a Windows-based tool that implements process hollowing and PPID (Parent Process ID) spoofing techniques. It allows for stealth execution of...
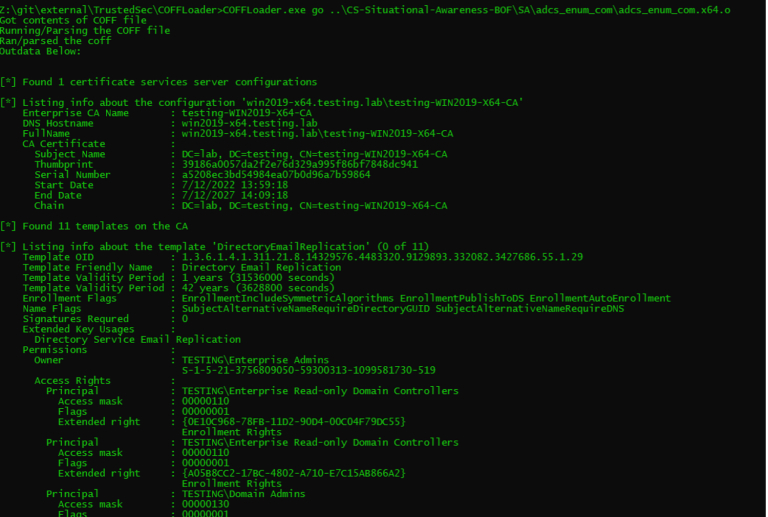
Beacon Object File (BOF) support has been at the cornerstone of capability for any modern C2 platform...